As cyberattacks against manufacturers increase, companies are being advised to raise their shields and pivot toward a zero-trust cybersecurity strategy. Five zero trust elements are highlighted.

Learning Objectives
- The convergence of IT and OT systems has created potential access points to OT systems that are vulnerable to cyberattacks.
- Industrial companies are begin encouraged to raise their cybersecurity shields and pivot toward a zero-trust approach.
- Elements of a zero-trust approach include multi-factor authentication (MFA), strong encryption and assessing risk through visibility.
Cybersecurity Insights
- There has been a considerable rise in cybersecurity attacks in the last several years that have touched everything from financial institutions, water treatment facilities, oil rigs and other critical infrastructure facilities.
- The idea that manufacturers have nothing of value when it comes to cybersecurity is simply not true. Some hackers are in it to cause damage for anarchistic or on behalf of an adversarial nation. Information, in some cases, is more valuable than money. Particularly if it’s sensitive company information.
- Companies need to adopt a zero-trust approach for cybersecurity and ensure access points are protected and there is a strong culture behind it. Cybersecurity is only as strong as the human element involved.
In February, the U.S. Cybersecurity & Infrastructure Security Agency (CISA), an arm of the Department of Homeland Security (DHS), issued an alert about cyberattacks on critical infrastructure in Ukraine and an advisory telling organizations to “put their shields up and take proactive steps to protect against active threats.”
CISA and the FBI, in a joint advisory, warned that attacks targeting organizations in Ukraine could easily spread beyond its borders and offered information on the malware being used, such as WhisperGate and HermeticWiper. The attacks in Ukraine lend further urgency in efforts to secure critical infrastructure in the United States and elsewhere, which has become a priority in recent years, particularly after last year’s Colonial Pipeline attack, which likely originated in Russia.
Over the past two years, the surge in ransomware attacks has hit healthcare organizations, financial institutions and a growing number of other high-profile organizations. Critical infrastructure has become a frequent target, including industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. In 2021 alone, 649 organizations in 14 of 16 critical infrastructure sectors suffered ransomware attacks, according to the FBI’s 2021 Internet Crime Report.
The Shields Up strategy issued by CISA outlines steps organizations should take in prevention, detection, response and resilience. It adds up that industrial companies need to adopt zero trust.
Many industrial companies already are working towards a zero-trust posture, but the industrial sector faces unique challenges in implementing zero trust principles of continuous authentication and authorization. Industrial leaders also need a thorough understanding of what a shields up/zero-trust strategy means for their companies. They need to know the necessary steps toward zero trust, the complications that can arise in the industry, and how to resolve them.
Critical infrastructure threats on the rise
The increasing threats to critical infrastructure, and the impact successful attacks can have on the nation’s economy and national security, have drawn the attention of Congress and the White House. President Joe Biden signed a law requiring critical infrastructure companies to report significant hacks to CISA within 72 hours of an attack and report ransomware payments within 24 hours. Another bill awaiting Biden’s signature as of this writing is the Better Cybercrime Metrics Act, which directs the Justice Department to categorize different types of cybercrime; create a framework for collecting incident reports from federal, state and local governments; and include questions about cybercrime in the annual National Crime Victimization Survey.
Aside from legal requirements, industrial companies have plenty of other incentives to secure systems. Ransomware and other attacks, which are becoming increasingly sophisticated and impactful, threaten a company’s business, reputation and bottom line. A successful attack can shut down operations (in Colonial’s case, for six days), steal vital information and intellectual property. This can result in sizable costs whether its in ransomware payments, system clean-up or restitution to customers.
While many companies understand the need for securing critical systems, but organizations can go wrong with implementations that don’t follow cybersecurity best practices or are misconfigured. With companies operating critical infrastructure, the task is compounded by a growing use of cloud applications, the expanding Industrial Internet of Things (IIoT), and the need to integrate security across enterprise IT infrastructure and operational technology (OT).
Where to start securing critical systems
To secure critical systems, organizations need to identify which systems are critical, an exercise that is not as simple as it might seem. The extent of automation, the links between on-premises and cloud systems, and how the IIoT is tied into a company’s network can greatly expand an organization’s attack surface. An HR or billing system, for instance, may not be critical on its own, but once it becomes interdependent with OT, it becomes essential by association. A skilled attacker who gains entry to any system, via a phishing campaign, for instance, could then infiltrate any other connected system.
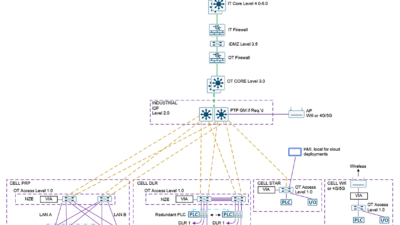
To fully assess risk, an organization’s leaders need to thoroughly understand systems within the enterprise, how systems connect and how they communicate with each other. For instance, industrial systems may once have been “air gapped” from the internet and in-house IT systems, but that has steadily changed over the years. OT and IT have converged using IT networking, IP and industrial controls system (ICS) protocols to boost interoperability and improve operational visibility. This improves efficiencies and leads to better decision-making and also increases vulnerabilities.
The presence of legacy systems also is a major concern. More than half of industrial sites still run operating systems no longer supported and thus go unpatched, such as Microsoft Windows XP. Even OT systems segmented from enterprise IT are vulnerable via open ports that don’t have proper access and protocol controls.
Once an organization has a complete grasp of its systems and their risks, the next step is to apply the same methodology of protecting access to all systems, whether critical OT systems or enterprise IT components. OT, which operates differently than IT, requires a separate layer for logical access and security. However, the level of protection must be the same. Applying security throughout the enterprise requires a unified, simplified and flexible approach built on a zero-trust strategy.
Five zero-trust elements
Zero trust grew out of the realization that traditional approaches to security, which focused on defenses at the network perimeter, didn’t hold up as IT operations expanded beyond the perimeter to the cloud. It became even more necessary with the addition of more mobile and remote users and data transactions occurring at the network edge. Zero trust focuses on continuously authenticating and authorizing users, devices, data, applications, and system services to protect those areas, each within a trust framework.
It combines strong multi-factor authentication with a fine-grained system of authorization that includes user role, time and location-based controls. Properly implemented, zero trust improves prevention, detection, response and resilience throughout the enterprise, including remote plant operations or a highly mobile workforce.
In getting to zero trust, industrial companies should include these five elements.
- Multi-factor authentication (MFA). One of the most beneficial protections against identity compromise is MFA, which combines some combination of passwords, tokens or biometrics. Companies should require MFA for network access, including user sessions involving any data in transit.
- Strong encryption. All communication between the IT network and the internet or the OT network should be encrypted. This should even include sometimes overlooked things, like browser-based thin-client access.
- Logging and monitoring. Organizations need to log and record all user access session data to critical OT systems, preferably in real-time, and closely monitor all remote user access sessions that aren’t read-only.
- Isolate protocols. Compromised credentials can result in severe damage. In 2016, the CrashOverride attack originating in Russia took down the Ukrainian power grid by exploiting compromised VPN credentials on an ICS system. The VPNs used in Ukrainian legacy ICS access controls were over 20 years old and never designed for regulating access to critical systems and applications. Isolating IT protocols and ICS protocols such as Modbus and DNP 3.0 to the OT network could have reduced the risk of stolen credentials.
- Assess risk through visibility. Asset monitoring, threat intelligence, indicators of compromise (IOC) feeds and vulnerability detection tools help an organization verify an acceptable risk level for critical assets.
Shields-up approach built on zero trust
Companies that provide critical infrastructure have become a prime target for an increasingly sophisticated breed of cyberattackers, many associated with nation-states or criminal organizations. Attacks on the energy, oil and gas, manufacturing, transportation and healthcare sectors can put lives at risk and disrupt a nation’s everyday operations, causing immediate and downstream effects on the economy and threatening national security.
OT systems used in industrial processes pose a particularly physical threat if they, for example, are involved in energy and gas distribution, the functionality of mass transportation systems or chemical mixing in manufacturing. The convergence of IT and OT systems has created potential access points to OT systems, many of them unpatched and with legacy virtual private network (VPN) access or virtual desktop infrastructure controls that are too complex and not secure enough to effectively manage access to the IIoT and the growing cloud infrastructures of many companies.
To secure critical infrastructure against the evolving threat landscape, industrial companies need to take a zero-trust approach for obtaining access to OT systems and any systems in the enterprises.
The shields up warning highlights the new reality for industrial companies, and zero trust is the path to putting those shields in place.
Bill Moore is CEO and founder at Xona. Edited by Chris Vavra, web content manager, Control Engineering, CFE Media and Technology, [email protected].
MORE ANSWERS
Keywords: shields-up, zero trust, cybersecurity
CONSIDER THIS
What cybersecurity approaches are your company taking?