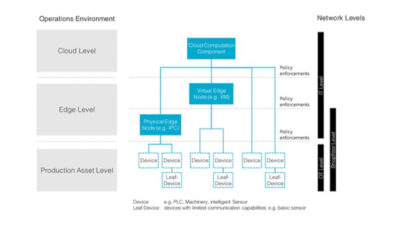
Effective network security is most successful when it is built up using a layered approach. Here we review common technologies and challenges for secure remote access, and examine one commercial device-based approach.
Security considerations are always a major issue when deploying a remote access solution, and the difficulties are compounded when solutions must include support for embedded systems. Successful implementations must provide effective authentication and access control, and care must also be taken to ensure that data is secured during transport over the network.
Additional considerations arise when target devices are hosted as guests on remote networks administered by others. In such cases particular care must be taken to ensure that your systems do not open the hosting network to outside threats.
Effective network security is not based on any one technology or component; it is most successful when it is built up using a layered approach, following the OSI Seven Layer Networking Model, with multiple defenses contributing to the overall solution. Here we review some common technologies for developing secure remote access solutions, along with some of the real-world challenges faced. We will also examine one commercial offering that addresses these challenges in an innovative and cost-effect way.
Network-based access controls
Network-based access controls are used to ensure that only authorized hosts are allowed to establish connections to your networked devices. Such access control usually takes the form of Firewalls that may work at Layer 2 (also referred to as the data link layer in the OSI Seven Layer Networking Model) or Layer 3 (the network layer).
Layer 2 solutions are sometimes described as “stealth firewalls”– they do not appear as a router hop to the network layer. Instead they provide a filtering capability on top of a transparent bridging connection between two network end points.
A layer 2 firewall may have Access Control Lists that allow the operator to control connections to or from specific devices or to prevent traffic for specific network protocols. For example, you may configure such a system to block IP-based traffic to a specific host while permitting Novell Netware IPX-based traffic.
Layer 3 firewalls, also known as port-based firewalls, operate at the TCP layer. When setting up a layer 3 firewall, the administrator configures Access Control Lists that enable or block connections based upon specified source and destination IP addresses and ports. Some so-called “Layer 3/Layer 4” firewalls function by examining the contents of layer 3 packets for additional information to help make their decisions.
Significant Issues with network layer access controls
The success of firewall technology in addressing external network threats did not come without a price – universal deployment of firewalls has greatly aggravated the difficulty of providing remote access to network devices.
Although effective and usually offering good performance, firewalls are complex to set up and administer and require network administrative privileges on the protected network. When setting up a layer 3 firewall it is common practice to enable connections to a device only on those ports that you know will be used. This can often lead to problems when a new service is enabled and the required port is being blocked.
The networking industry’s initial response to the growing remote access challenge was the virtual private network (VPN). As its name implies, a VPN replaces dedicated leased lines, cellular links or other costly physical connections with a secure mechanism over which traffic from a remote device can be tunneled to the target network using an existing network connection.
As with firewalls, installing and operating your own VPN requires network administrator privileges. Both IPSec and SSL VPNs are “IT-oriented” solutions, used by network administrators to control access into their networks. Thus, installing such a device at each remote location is usually not an option for enabling remote access to devices on other people’s networks. Another issue for SSL VPN solutions is the challenge of maintaining large numbers of user-level security credentials for each support technician when accessing equipment at a large number of locations.
A final significant issue for VPNs when used to grant guest access is that once a VPN connection is established, the remote host essentially becomes another node on the remote network. This can be a problem when the goal is to grant limited access privileges to specific hosts.
One solution is to group guest devices onto their own local area network (LAN), but this is often not possible when your equipment is being hosted on networks outside your own administrative control.
Machine-to-machine remote management
One commercial offering that addresses these challenges is a machine-to-machine remote management device capable of providing easy yet secure remote Internet access to IP-enabled equipment– even when such equipment is located behind remote firewalls or a VPN. Readily adaptable to a wide range of management tasks, such devices are suited for accessing and managing embedded systems located on remote customer networks. They are also appropriate where support staff do not have administrator privileges on the remote network.
The ManageLinx management platform from Lantronix is one example. Its patent-pending ManageLinx VIP Access component provides transparent Layer 3 network access to any piece of remote equipment without specialized client software or network reconfiguration. Because it is able to work with any TCP/IP-enabled application running on any host or operating system, ManageLinx VIP Access is particularly useful for embedded systems deployments where dedicated VPN clients or specialized networking configuration changes are not an option.
ManageLinx works over conventional Internet connections with as little as one open port to the WAN and requires no reconfiguration of the target network’s firewall settings. Because it can use existing Internet connections, ManageLinx VIP Access eliminates the need for dedicated analog phone lines or cellular coverage.
Because the ManageLinx VIP Access operates at the Network layer and communication between VIP address and the endpoint device is fully automated, it is easy to integrate embedded devices into the system. No dedicated clients or specialized software is needed to access the system. Embedded systems programmers utilize traditional TCP/IP programming mechanisms:
With multiple defenses contributing to the overall solution, effective network security is attainable. Investigate the layered approach. With care, it is possible to provide effective, secure network access to remote access deployments, enabling new service models and increasing customer capabilities.
Errett Kroeter is director of corporate & channel marketing for Lantronix in Irvine, CA. [email protected] . Additional information on the new ManageLinx VIP Access remote access solution, including a security white paper and a remote product services case study, are available at the Lantronix website .
Remote Control: Get Behind firewalls securely.
Renee Robbins , senior editor Control Engineering News Desk Register here and scroll down to select your choice of eNewsletters free .