Industrial wireless tutorials: The Open Systems Interconnection (OSI) model is a conceptual model used to organize the various functions of data communications by segregating the distinct functions into a seven-layer model from the Physical layer. Learn how the OSI model relates to industrial wireless communications.
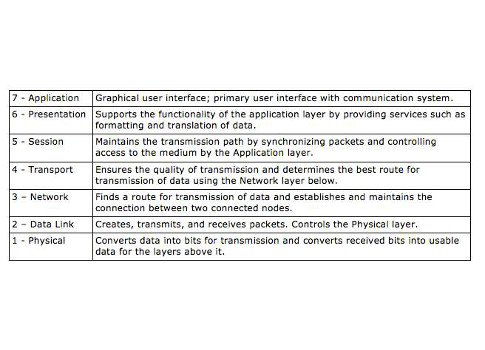
As we discussed in the last segment, WLANs operate at the physical and data link layers of the OSI model. For those readers unfamiliar with the model, it is a conceptual model used to organize the various functions of data communications by segregating the distinct functions into a seven-layer model from the Physical layer (wired or wireless medium) up to the Application layer, where the end user device, such as a PC, resides. The layers, from the top, are: Application, Presentation, Session, Transport, Network, Data Link, and Physical. Unfortunately, space does not allow for a full discussion of the functions of each layer.
| Layer name | Description |
| 7 – Application | Graphical user interface; primary user interface with communication system. |
| 6 – Presentation | Supports the functionality of the application layer by providing services such as formatting and translation of data. |
| 5- Session | Maintains the transmission path by synchronizing packets and controlling access to the medium by the Application layer. |
| 4 – Transport | Ensures the quality of transmission and determines the best route for transmission of data using the Network layer below. |
| 3 – Network | Finds a route for transmission of data and establishes and maintains the connection between two connected nodes. |
| 2- Data Link | Creates, transmits, and receives packets. Controls the Physical layer. |
| 1- Physical | Converts data into bits for transmission and converts received bits into usable data for the layers above it. |
As data is passed down the stack from sending to receiving computers, it is encapsulated with information or data that is used by each succeeding layer; on the receiving side, the encapsulation is stripped off as the data proceeds from the Physical layer to the Application layer. For instance, a file is sent from Computer A to Computer B. As the file leaves the Application layer and enters the Presentation layer, it is wrapped with a new header and trailer containing the instructions or status bits in a specified manner and in a specified position relative to the file, which is called the payload. In a TCP/IP network, the Transport layer examines the data it receives from the upper layers to determine the best route to Computer B. It then determines if the data exceeds the maximum transmission unit (MTU) size. If it does, then the data is broken into segments, each assigned a unique number. This process ensures that the data is received and reassembled in the right order.
The Transport layer then sends the data to the Network layer (sometimes called the Internetwork layer) for routing to the receiving computer. The Transport and Network layers mark the boundary between data processing and data communication in the system. The Network layer passes the data, now called a packet, or datagram, to the Data Link layer, which adds addressing data and control information to the datagram, creating a frame. The frame is then passed to the Physical layer, which puts the frame on to the medium using various techniques. At the receiving end, the process is reversed.
All Wireless LANs operate on the Physical and Data Link layers, layers 1 and 2. All Wi-Fi systems use these layers to format data and control the data to conform with 802.11 standards. Medium arbitration-controlling when the AP can access the medium and transmit or receive data-is done at these two layers. We will discuss the very complex technique of wireless medium arbitration in a future segment; for now, it is important to understand the functions of layers 1 and 2.
The Physical layer, or PHY, is the medium through which communication is effected. It is at this layer the transceiver is controlled to access the medium. We are primarily concerned with the wireless medium. Unlike a bounded, wired medium, WLANs operate “over the air” and are subject to an entirely different set of rules for accessing and controlling the medium. For instance, wired networks have the ability to detect and mitigate data collisions; wireless networks cannot detect collisions, instead, elaborate protocols are in place to allow access and control of the medium and to avoid collisions. Wireless networks are also subject to unintentional interference and intentional disruptions. Wired networks are relatively difficult to hack into while wireless networks can be casually hacked by anyone with a wireless card within range of an access point. These issues have provided developers with significant challenges to overcome to ensure that WLANs are reliable and secure.
The Data Link layer consists of two sublayers: the Logical Link Control (LLC) sublayer and the Medium Access Control (MAC) sublayer. The LLC receives an IP packet from the Network layer above it and encapsulates the data with addressing and control information. This packet, now called a frame, is passed to the MAC, which modifies the addressing and control information in the frame header to ensure the data is in the proper form for application to the Physical layer. The MAC then passes the frame to the PHY, which modulates the data according to the PHY standard in use (DSSS, OFDM), and transmits the bits as RF. The process is reversed at the receiving end.
Upon successfully receiving the transmitted data, it is demodulated and the resulting frame is passed to the receiving MAC. The frame header is examined to determine if it is the intended address; if it is, then the MAC data is stripped off and passed to the LLC, which then examines the upper-level addressing data in its header. It strips off its data and passes the packet to the Network layer, which performs the proper routing to the destination on the local network.
This all happens within an average time span of 500 milliseconds, unless QoS protocols are in play, in which case the processing time is significantly reduced. Unfortunately, congested networks will cause excessive arbitration for control of the medium, resulting in latency and extended transaction times.
– Daniel E. Capano, owner and president, Diversified Technical Services Inc. of Stamford, Conn., is a certified wireless network administrator (CWNA). Edited by Chris Vavra, content specialist, CFE Media, Control Engineering, [email protected].
ONLINE extras
Home has other wireless tutorials from Capano on the following topics:
Wireless propagation fundamentals
Wi-Fi standards
Radio antenna types
Upcoming Webcasts has wireless webcasts, some for PDH credit.
Control Engineering has a wireless page.