Supervisory control and data acquisition (SCADA) systems’ traditional role is changing as the Industrial Internet of Things (IIoT) continues to take a larger role. SCADA systems were not originally designed for cybersecurity and plants need to adjust to this new reality.
Supervisory control and data acquisition (SCADA) systems, and the broader industrial control systems (ICS) including SCADA, human-machine interfaces (HMIs), building management systems (BMS), manufacturing execution systems (MES), and computer maintenance management systems (CMMS) have roots in proprietary technology that was traditionally isolated from the enterprise information technology (IT) infrastructure. These platforms were not originally designed for cybersecurity.
The ICS’ traditional role of control and safety has expanded to include providing plant and process information or responding to direction from ERP and other enterprise systems. This, however, has exposed the ICS to potential cyber threats, according to "Security the Move to IP-Based SCADA/PLC Networks" by the Centre for the Protection of National Infrastructure. The current focus on connectivity under the banner of the Internet of Things (IoT), and the closely related Industrial Internet of Things (IIoT) or Industrie 4.0, has a huge potential benefit to data aggregation strategy and situational awareness. However, IIoT devices use Internet Protocols (IP), which further increases the exposure to cyber threats.
The IIoT transformation is disrupting the role of the traditional control room with a trend toward mobile devices that are used for monitoring and control (Nugent, Bailliencourt, and Kaltenbacher, 2015). The emerging contextual HMI component of IIoT-enabled ICS provides great productivity gains to operations and maintenance organizations, while expanding the perimeter of the ICS. However, it adds to the scope of cyber threat management.
Cybersecurity pillars
The modern ICS platform vendor incorporates the Software Engineering Institute’s Cyber Risk and Resilience Management into the ISO 9001 Quality Process for development and production. The goal is to be transparent regarding internally or externally reported vulnerabilities and to act quickly to minimize risk for customers.
Participation in standards organizations, such as the Institute of Electrical and Electronic Engineers (IEEE) and the International Electrotechnical Commission (IEC), are designed to assist in achieving the goal of transparency through open discussion and feedback. Participation is critical to rapid implementation of the recommendations coming from these organizations.
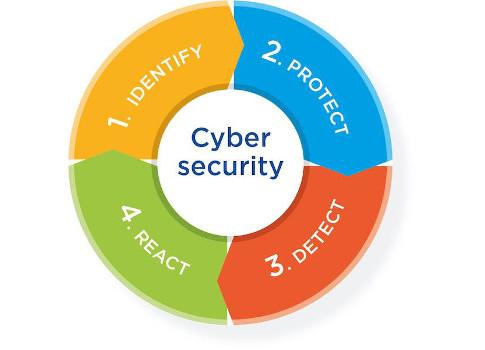
The National Institute of Standards and Technology (NIST) has provided a framework that is invaluable for systematically identifying an organization’s critical assets, identifying threats, and securing critical assets (Nugent and Hoske, SCADA cybersecurity, 2015). The framework has four elements: Identify, protect, detect, and react.
Recognize and identify suspicious behavior
Prior to the 2016 Boston Marathon, the National Nuclear Security Administration (NNSA) performed a background radiation assessment using low flying helicopters. The measurement of naturally occurring radiation to establish baseline levels is a normal part of security and emergency preparedness (National Nuclear Security Administration, 2016).
It is important to have an inventory of assets and data flows to establish a baseline of normal behavior for ICS. Industrial networks can be large and complex, and industrial protocols are different than those of the enterprise IT networks. Automated tools that map and monitor the network equipment using simple network management protocols (SNMP) improves the efficiency and accuracy of the inventory.
Inventory and monitoring tools that are control-system aware are an important factor in establishing a reliable ICS baseline. Monitoring the ICS with technology that is capable of producing a baseline template of the communication between the ICS, the PLC, and other control elements is critical. Ideally, such systems will be able to:
- Extract metadata from the network flow using passive sensors
- Dynamically build a visual inventory of components and a map of connections
- Learn the ICS and provide statistical and behavioral descriptions of normal operations
- Recommend preventative actions
- Trigger incident response upon evidence of compromise.
The IIoT devices often communicate using wireless technologies. A difference between general IT networks and ICS networks is the use of static IP. As industrial networks become connected to the broader Internet, health monitoring systems look for changing or duplicate IP and MAC addresses, device or cable movement, and unauthorized connections. This environment is greatly complicated with the addition of mobile sensors connected through wireless access points with dynamic IP connections (Robles and Kim, 2010).
Protect the dissolving perimeter
At a recent Tech Talks Summit in Massachusetts, Mike Ratte discussed today’s IT security landscape (Centrify, 2016). He said, "Identity is the new perimeter," and his arguments for that include:
- Nearly half of breaches are caused by compromised credentials
- Hackers target all classes of users including privileged users
- Traditional perimeter-based security is not enough
- Security should be based upon context-based policies.
This strategy fits well with the dissolving perimeter of the ICS, which has embraced the benefits of open connectivity and therefore also will benefit from enterprise security professionals.
With 63% of confirmed data breaches involving weak, default, or stolen passwords (Verizon, 2016), credential management ranks high on the list of ICS cyber threats. The possibility of physical access through stolen or lost mobile devices compounds the need for strong credential management.
Industrial networks provide the first level of defense with firewalls, virtual private networks (VPN), and switches. The ICS vendor must encrypt configuration files, provide monitoring of unusual connection attempts, use secure protocols such as HTTPS, and provide advanced user rights integrated with Microsoft Active Directory.
With these capabilities in place, the ICS can fit into a strong identity management world. With Active Directory as the core identity management repository, it is now possible to use one sign-on for all applications associated with an ICS user.
Context-based policies are the cornerstone of the management of mobile workers. The required rights of operations and maintenance workers vary by work zone. An ICS mobility server that manages the access to resources based on geographical zone, and is synchronized with active directory, ensures that tight contextual policies are enforced.
One last point has to do with the failure to manage onboarding and off-boarding of users and accounts. For example, a contractor coming into a facility may have a temporary account set up that is left open in case the contractor needs to return at another time. This may be done because it is difficult to onboard and off-board when there are "islands of identity." Central identity management eliminates orphaned accounts, eliminates the need to use root passwords, and eliminates islands of identity. This makes onboarding and off-boarding significantly more manageable and integrated with corporate credential policies.
Detect abnormal, suspicious behavior
With a clear inventory of assets and baseline of templates representing network and application behavior, the industrial network monitoring system is prepared to identify when things look suspicious. When baseline templates are compared in real-time to the ICS operation, the system can raise alarms and act quickly on threat of compromise.
There is another aspect of detection that is part of the trend toward mobility. Mobile device management (MDM) is used by enterprises to deploy policies consistent with the rights of the mobile worker. An example would be to have a policy to turn off the device camera when at work but allow it when off-site.
The best-of-class solutions have active security so that the device can respond to threats even when disconnected from the network. These systems actively detect rooted and jailbroken devices. They also detect man-in-the-middle attacks, silently compromised conditions, lost or stolen devices, and network attacks (ViaSat, 2016).
Minimize damage, ensure recovery
For the mobile device, automated response includes locking or wiping the device, rebooting to a safe state, or disabling network access. Best-of-class systems also notify security and operations personnel when a threat is detected.
It is important to have strong version control so that it is possible to restore to a safe reference point after an incident. Version control deployed on a secure server helps maintain the integrity of the configuration and provides traceability for any changes made to configuration files.
Unfortunately, restoring to a previous version may, depending on where the operational data is stored, result in a loss of historical data. Redundant controllers, networks, historians, and communication servers have long been the hallmarks of best-of-class SCADA. This, however, is not sufficient against cyber threats, which compromise primary and backup elements.
The use of virtual machines (VM) for hosting the ICS is designed to mitigate the risk of data loss. By deploying disaster recovery as a service (DRaaS) on the VM, the time to recovery can be as short as 15 minutes (Veeam, 2016). Because the time between intrusion and detection is trending in the wrong direction (Verizon, 2016) this may still result in loss of data.
Stopping the bad guys through strong credential management and intrusion protection are still the best ways to secure SCADA in the age of IoT.
Ed Nugent, chief operating officer, PcVue Inc.; Mike Ratte, regional manager, Centrify Corp. Edited by Chris Vavra, production editor, Control Engineering, CFE Media, [email protected].
MORE ADVICE
Key Concepts
- The Industrial Internet of Things (IIoT) and Industrie 4.0 have a lot of potential for SCADA systems, but they also have potential cybersecurity risks.
- NIST’s framework for systematically identifying an organization’s critical assets has four elements: Identify, protect, detect, and react.
- Strong intrusion prediction and credential management are the best ways to secure SCADA systems.
Consider this
What other methods can be taken to secure SCADA systems in the IIoT and Industrie 4.0 era?
ONLINE extra
References
Centre for the Protection of National Infrastructure. Securing the Move to IP-Based SCADA/PLC Networks. London: Centre for the Protection of National Infrastructure, 2011.
Centrify. Centrify Overview and Company Strategy, 2016.
National Nuclear Security Administration. NNSA to conduct Aerial Radiation Assessment Survey over Boston area, March 31, 2016. Retrieved from National Nuclear Security Administration Press Release.
Nugent, E., and Mark T. Hoske. "SCADA cyber security." Control Engineering, 42-43, July 2015.
Nugent, E., P. Bailliencourt, and A. Kaltenbacher. The Architecture of the SCADA Mobility Infrastructure, July 28, 2015. Automation.com.
Robles, R. J., and T.H. Kim. "Architecture for SCADA with Mobile Remote Components." Proceedings of the 12th WSEAS International Conference on Automatic Control, Modelling and Simulation, 346, 2010.
Veeam. The Always On Enterprise, 2016. Retrieved from Veeam:
Verizon. 2016 Data Breach Investigations Report, 2016.
ViaSat. Mobile cybersecurity for remote workforces, 2016. Retrieved from ViaSat.
About the Authors
Ed Nugent is the Chief Operating Officer of PcVue Inc. of Woburn, Ma., and the North American supplier of PcVue Solutions for SCADA, BMS, and HMI powered by ARC Informatique. Nugent has more than 35 years’ experience in development and deployment of industrial control systems with a patent pending for Contextual Mobility. He is an alumnus of the University of Wisconsin, College of Engineering, and the University of Puget Sound where he earned his MBA.
Mike Ratte is the New England and Upstate NY Regional Manager of Centrify Corp. of Santa Clara, Calif. Ratte has over 25 years’ experience in the IT industry with more than 12 years in IT security. He is holds a degree in Economics from Framingham State University.
See additional cybersecurity stories linked below.

