The convergence of IoT, edge computing and digital twin technology is transforming real-time process safety monitoring and response. These technologies enhance hazard detection, improve safety system resilience and address the cybersecurity challenges that arise as safety infrastructure becomes increasingly interconnected.
Process safety insights
- Digital twin, IoT and edge computing all empower hazard detection, improve safety system resilience and address the cybersecurity challenges that arise as safety infrastructure becomes increasingly interconnected.
- IoT, edge computing and digital twin technologies can only be successful if companies strategize to use them appropriately.
- It’s critical to utilize process safety technologies responsibly to avoid cyberattacks.
There was a time when process safety relied almost entirely on the sharp eyes and quick reactions of seasoned workers on the factory floor. But technology is changing that equation. Today, interconnected sensors, real-time analytics, and predictive modeling are transforming how industries detect, prevent, and respond to hazards.
The convergence of IoT (Internet of Things), edge computing, and digital twins is rewriting the rulebook for process safety. These innovations allow safety teams to move from reactive to proactive, using real-time monitoring, automated decision-making, and virtual simulations to catch risks before they escalate. And the industry is taking notice, with 95% of professionals affirming that digital tools are essential in enhancing process safety.
While these technologies offer unprecedented visibility and control, they also introduce cybersecurity vulnerabilities that must be managed.
How IoT, edge computing and digital twins enhance safety
The integration of IoT, edge computing and digital twins has created a new ecosystem where they work together to improve safety and prevent incidents before they happen.
Here’s a quick look at these technologies (see Figure 1).
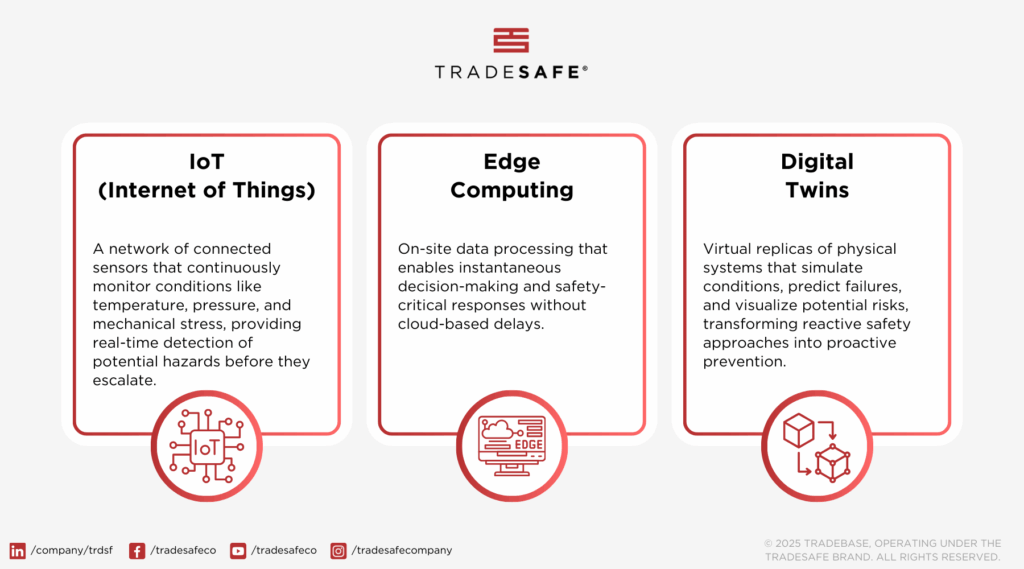
- IoT (Internet of Things) connects sensors, machines, and systems, enabling real-time data collection and communication. Think of IoT as a network of digital eyes and ears that detect pressure fluctuations, temperature changes, gas leaks and mechanical stress before they escalate into major hazards.
- Edge computing keeps the decision-making closer to the source, allowing safety-critical responses to happen instantaneously.
- A digital twin is a virtual replica of a physical asset, process or system designed to simulate real-world conditions. By analyzing sensor data and predicting failures before they occur, digital twins give safety teams a crystal ball view of potential risks, allowing proactive interventions rather than reactive fixes.
Together, these technologies improve efficiency and change how industrial safety is managed. The ability to track safety conditions as they change in real time is critical to preventing disasters before they unfold.
In chemical processing plants, for example, IoT sensors can detect small leaks before they turn into full-blown gas releases. Edge computing processes this data locally, triggering an immediate containment response without waiting for cloud-based analysis. Meanwhile, a digital twin of the plant can simulate potential leak scenarios, helping engineers identify weak points before they fail.
IoT, edge computing and digital twins in action
Industries worldwide are actively using these technologies to prevent hazards, optimize maintenance, and respond to emergencies faster than ever before. Below are compelling examples demonstrating how these innovations are reshaping process safety across different sectors.
Thermal imaging for hazard detection
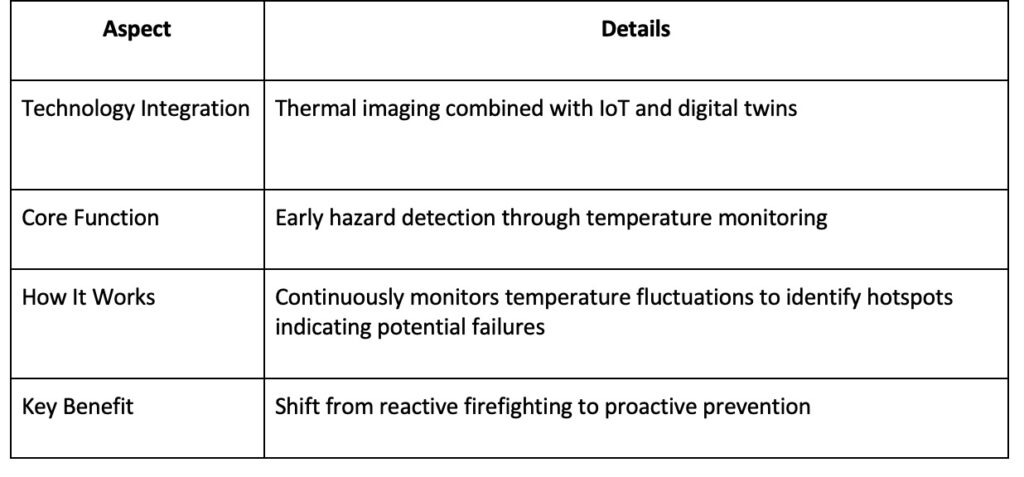
Thermal imaging, when integrated with IoT and digital twins, has become a powerful tool for early hazard detection in various environments.
A recent study explored the development of a predictive digital twin for condition monitoring using thermal imaging. This system integrates advanced mathematical models with real-time thermal data to detect anomalies in industrial equipment.
By continuously monitoring temperature fluctuations, this technology identifies hotspots that could indicate potential failures, such as overheating machinery or electrical faults, before they turn into catastrophic incidents.
For instance, consider a chemical processing plant where pipelines carry volatile substances. An IoT-enabled thermal camera can detect an abnormal rise in temperature due to friction, corrosion, or leaks. When this data is processed using edge computing, an immediate alert can be triggered to shut down the affected section before a fire or explosion occurs. Meanwhile, the digital twin of the facility can simulate the leak’s potential spread, helping operators preemptively mitigate risks (see Table 1).
Table 1: Thermal Imaging for Hazard Detection
Predictive maintenance with digital twins
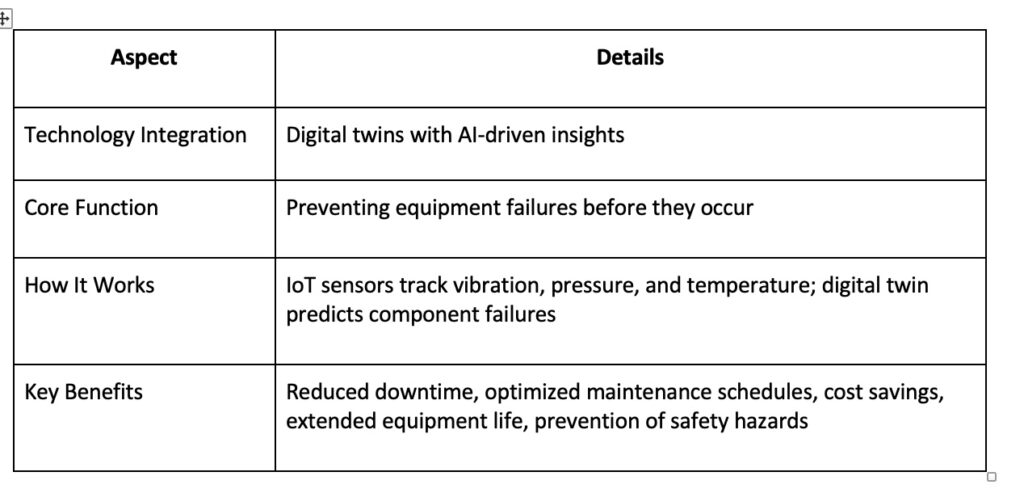
Unplanned downtime is a major concern for industries reliant on complex machinery. Predictive maintenance, powered by digital twins and AI-driven insights, is changing how companies prevent failures before they happen.
Siemens recently advanced its Senseye Predictive Maintenance solution by incorporating generative artificial intelligence (AI). This enhancement allows maintenance teams to interact with digital twins in a more intuitive, conversational way, making it easier to anticipate equipment failures and schedule necessary interventions. As a result, companies reduce downtime, optimize maintenance schedules and cut costs.
An application of this technology can be seen in rotating equipment like pumps and compressors. In the past, operators relied on manual inspections and scheduled maintenance cycles, often replacing parts too early (leading to unnecessary costs) or too late (resulting in unexpected failures).
With IoT sensors tracking vibration, pressure and temperature, a digital twin can predict when a component is nearing failure. Edge computing ensures this information is processed in real time, sending alerts for maintenance only when truly needed. This not only extends equipment life but also prevents safety hazards caused by mechanical failures (see Table 2).
Table 2: Predictive Maintenance with Digital Twins
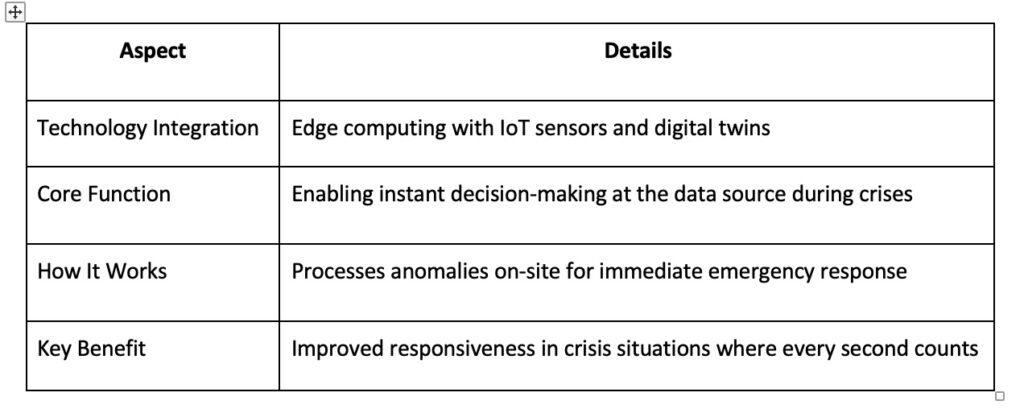
Edge Computing in Crisis Response
Delays in detecting and responding to a crisis, whether it’s a gas leak, equipment failure, or environmental hazard, can lead to severe consequences. This is where edge computing becomes indispensable by enabling instant decision-making at the source of data generation.
A recent study introduced a digital twin-driven anomaly detection framework based on edge intelligence. This system allows industrial environments to detect and respond to anomalies in real-time, significantly enhancing safety and reliability.
Consider handling a volatile chemical. If an IoT sensor detects an abnormal pressure spike in a pipeline, traditional cloud-based systems might take seconds (or longer) to analyze the data and trigger a response. However, with edge computing, the anomaly is processed on-site, allowing for an immediate emergency shutdown before a rupture occurs.
Moreover, a digital twin of the refinery can simulate how the pressure buildup will affect surrounding systems, giving engineers insights to adjust operations before an accident happens. This level of responsiveness is invaluable in crises, where every second counts.
One real-world example of edge computing’s impact can be seen in oil and gas drilling operations. When IoT sensors detect early signs of a wellbore collapse or gas influx, edge computing can automatically halt drilling activities, preventing blowouts and ensuring worker safety (see Table 3).
Table 3: Edge computing in crisis response
Using IoT, edge computing and digital twins to combat cyberthreats
As industries embrace IoT, edge computing, and digital twins to enhance safety, they must also confront the cybersecurity risks that come with increased digital connectivity. While digital transformation enables real-time monitoring and predictive insights, it also widens the attack surface for cyber threats (see Figure 2).
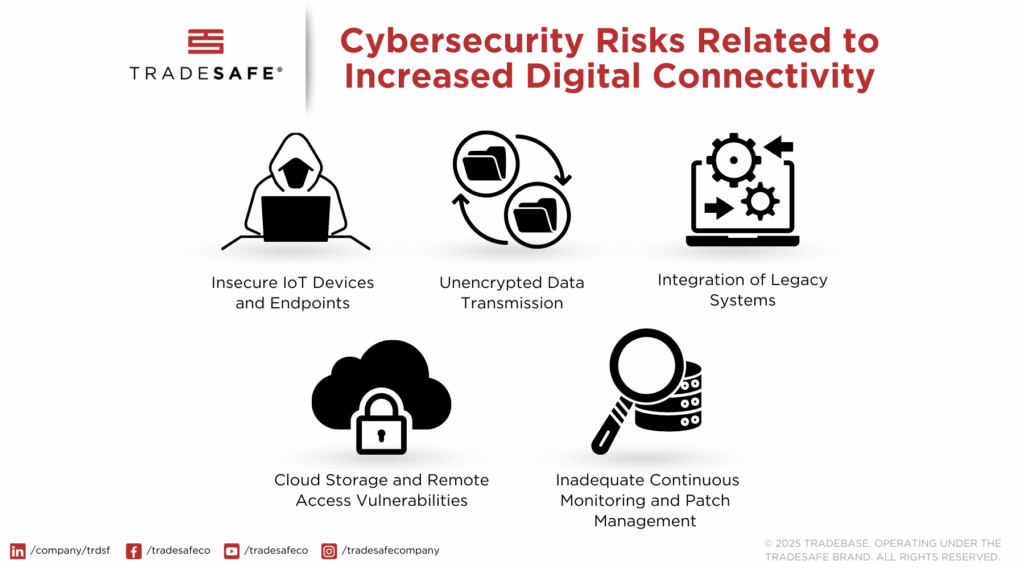
1. Insecure IoT devices and endpoints
The widespread adoption of IoT in industrial environments has significantly increased the number of attack points. More than 50% of IoT devices contain exploitable vulnerabilities, making them prime targets for hackers seeking to gain access to critical infrastructure.
These threats can be mitigated by:
- Disabling default credentials and requiring unique, complex passwords on all IoT endpoints.
- Protecting access to critical systems by adding a Multi-Factor Authentication (MFA).
- Conducting routine firmware updates and vulnerability assessments to close security gaps.
2. Unencrypted data transmission
Many connected devices transmit sensitive process safety data without encryption, making them vulnerable to interception. Attackers can alter safety-critical information, causing false alarms or disabling real-time hazard detection.
These threats can be mitigated by:
- Implementing strong Transport Layer Security (TLS) encryption for all data transmitted between devices.
- Using Virtual Private Networks (VPNs) or encrypted communication channels to prevent unauthorized interception.
- Ensuring only verified devices and personnel can send or receive safety-critical data.
3. Integrating legacy systems
Many industrial facilities still rely on legacy equipment that was never designed with cybersecurity in mind. A report found that 40% of organizations have at least one outdated OT asset connected to the internet with known vulnerabilities.
These threats can be mitigated by:
- Isolating legacy systems using firewalls to prevent them from exposing the entire network to attacks.
- Deploying dedicated security gateways that act as a bridge between old and new systems, filtering out potential threats.
- Gradually replacing obsolete equipment with modern, cybersecurity-ready alternatives.
4. Cloud storage and remote access vulnerabilities
The growing reliance on cloud platforms and remote access tools has increased cyber risks. Attackers exploit misconfigured cloud storage or weak remote access controls to steal sensitive operational data. Verizon’s 2024 Data Breach Investigations Report highlighted a surge in breaches initiated by exploited vulnerabilities in remote access tools.
These threats can be mitigated by:
- Using VPNs and strict access policies to control who and what can connect to safety systems.
- Requiring MFA for all remote logins, ensuring only authorized personnel can access critical assets.
- Continuously monitoring cloud-based systems for misconfigurations and apply security patches immediately.
5. Inadequate continuous monitoring and patch management
Slow patch cycles leave industrial systems vulnerable for extended periods. According to Verizon’s 2024 Data Breach Investigations Report, it takes organizations an average of 55 days to patch just 50% of their critical vulnerabilities, leaving them exposed to attacks for weeks or months.
These threats can be mitigated by:
- Using automated update systems to apply security patches as soon as they’re available.
- Deploying real-time monitoring solutions to detect anomalies and potential breaches.
- Simulating cyberattacks to identify weak points before real hackers do.
By shortening patch cycles and actively monitoring systems, companies reduce their exposure to cyber threats.
Strategizing to get the most of IoT, edge computing and digital twins
Technology has already transformed process safety, but its full potential lies in how we choose to apply it. IoT, edge computing and digital twins give us the ability to detect hazards in real time, predict failures before they happen and respond faster than ever before. Yet these tools are only as effective as the strategies behind them.
As industries move forward with digital transformation, safety professionals must ask themselves: are we truly using these innovations to their fullest potential? The next time you’re on the factory floor, in the control room, or reviewing compliance reports, consider this. Could a sensor, a simulation or a smarter response system prevent the next incident? If the answer is yes, then the next step is clear. It’s time to act.
But with these advancements comes a critical responsibility: making sure that technology enhances safety without introducing new risks. Are we moving fast enough to secure the very systems designed to protect us? In process safety, being proactive is an advantage that can make the difference between preventing an incident and reacting to a disaster.
Herbert Post is the vice president of TRADESAFE. Edited by Sheri Kasprzak, managing editor, Automation and Controls, WTWH Media, [email protected].



