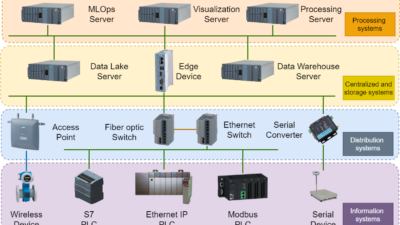
Industrial Internet of Things (IIoT) security should be a priority for every manufacturer and not left on the backburner. Every device potentially can be hacked.
Learning Objectives
- Internet-connected devices are at increased risk for cyberattacks as the Industrial Internet of Things (IIoT) becomes more prominent.
- A communications platform as a service (CPaaS) can help companies coordinate against potential cyberattacks and give users better coordination.
- A secure access service edge (SASE) combines a cloud-based and centralized system for policy management as well as local enforcement of identity-driven services.
Any internet-connected device can be targeted, hacked and exploited for nefarious purposes. Worse, as the industrial internet of things expands, more devices—potentially with inferior security standards—are being connected to it. This effectively lowers the technical bar for bad actors with malicious intent, and means attacks on IIoT devices will escalate, especially as more smart devices are connected. The bottom line: IIoT security should be a priority for every manufacturer. Communications platform as a service (CpaaS) and secure access service edge (SASE) can help.
As manufacturers embrace digital transformation and the technology that drives Industry 4.0, the Industrial Internet of Things (IIoT) has accelerated some salient features of this transformation, including Big Data, artificial intelligence (AI) and machine learning (ML). In any modern plant today, IoT devices connect, control and monitor manufacturing assets. They facilitate production flow, monitor development cycles and manage warehouses as well as inventories.
Cellular IIoT can be better than Wi-Fi: 3 examples
While connectivity technologies like Wi-Fi can support many of these IIoT applications, manufacturers are looking to 4G LTE or 5G NR cellular technologies to set up private cellular networks that provide them with additional connectivity capabilities for IIoT applications. Here are just three of the examples where cellular IIoT is more applicable than Wi-Fi:
Limitless connectivity in robots. Consider a manufacturer building line marking robots that are shipped all over the world. Before shipping, a SIM needs to be inserted into every robot. There are different network providers in every country with different signal availability. The manufacturer would have to evaluate which SIM card needed to be inserted in which robot based on its destination.
Smart grids. Cellular IIoT makes it possible to monitor network-connected machines and plants, and well as mobile devices and mobile machines over a mobile network connection. This approach enables smart grids to be distributed much more granularly throughout the world.
Predictive maintenance (PM). PM increases operational efficiency and reduces unplanned downtime. Cellular connectivity provides the dependable and predictable environment needed to support a fleet of sensors at high data rates, enabling predictive maintenance in manufacturing. Cellular is helpful in environments whose infrastructure can no longer support traditional means of connectivity.
However, there’s a catch to all this: the millions of IoT devices that enable these use cases are attractive attack surfaces. An attack surface is any point or part of the system through which an unauthorized user or attacker can try to get into the system. Within an IoT solution there are numerous attack surfaces: the device, the wireless module, the data transmission from the device to an application, the application infrastructure, and the application itself. Any of these can be used to impact access, misuse or abuse the system, and to access or modify confidential information.
Look at industrial services for cybersecurity risk mitigation
IoT hacks and cyberterrorism are a worrisome trend. These potentially devastating security breaches make strong IoT security an imperative for manufacturers. The latest technologies, such as communications platform as a service (CPaaS) and secure access service edge (SASE) can help manufacturers keep their connected devices secure, but to counter the evolving range of cybersecurity threats, security experts must evolve their security smarts by:
- Understanding how and why their IoT applications and devices are vulnerable to hacking attempts
- Learning from past IoT security failures
- Applying modern solutions and strategies to harden the security of their devices and applications.
Examine the industrial network for vulnerabilities
One reason why IoT devices are so vulnerable to hacking attempts is the security—or lack thereof—of the network to which they are connected. Manufacturers rarely use the public internet to communicate, but private networks are just as susceptible to substandard security standards. Even if your network traffic is unencrypted, malicious actors can compromise IoT devices with these techniques:
Eavesdropping and traffic sniffing: Poor encryption settings for data transmission makes your communication vulnerable to hackers who want to read, steal, or otherwise tamper with your data. This is a significant security threat for IoT networks as regular transmissions between and among devices are often not encrypted. While encryption may not be needed for devices that do not store sensitive data, an unsecured device and its unencrypted transmissions can still provide a hacker with an entry point into your wider network.
DNS poisoning: Another common threat stems from compromised public domain name systems (DNS). DNS poisoning is a tactic employed by malicious actors to divert and re-route communication between devices away from a legitimate application server to a spoofed one.
Distributed denial of service (DDoS): A DDoS attack is a well-documented approach by which a server is inundated with redundant requests, which overloads its capacity and takes it completely offline. A DDoS is often carried out from a botnet that previously breached servers and computers have been subsumed.
Unprotected SIM: Remote cellular IoT devices may be located in publicly accessible locations, such as sensors and meters, where a bad actor can easily snatch them, breach them and steal the SIM card held inside the device and use it to tap into the company’s data.
Calling home to base: Similarly, once malware has infected a device, it can re-program the device to “call home” to the hacker’s base, sending sensitive data to malicious actors without the user’s knowledge and consent.
Humans in the loop: Cybersecurity training for operators, others
Hackers are skilled at exploiting one of the weakest links in the security chain: humans. People, even seasoned security professionals, may opt for convenience over bulletproof. This may be intentional; they don’t want the hassle of complex passwords and the need to frequently change them.
It bears repeating password hygiene is crucial along with effective policies that require human operators to use hard-to-crack passwords (or multi-factor authentication) that are beyond the scope of a brute force attack.
Past cybersecurity breaches teach valuable lessons
Even though the technology used by hackers continues to evolve and new zero-day exploits are discovered daily, security professionals can still learn valuable lessons by analyzing past security breaches and applying lessons learned to their network and security policies.
Part and parcel of this effort is understanding (or trying to understand) the motivations of malicious actors for intruding into your network. While the recent hack of the Colonial Pipeline was aimed at extorting ransom payments, other attacks like the 2016 Mirai botnet case were about wreaking havoc. In 2016, a type of malware was being disseminated across the internet.
It eventually subsumed over 145,000 IP cameras into a botnet and instigated DDoS attacks against the servers of the computer game Minecraft and the websites of companies such as Netflix, Twitter and Reddit. This sort of attack could equally be aimed at a manufacturer’s critical assets.
Deficient network topologies, security protocols
A surprisingly large number of IoT network connectivity models rely on an approach that routes traffic first through the central local area network (LAN) and then to the wide area network (WAN) to the individual device’s location. This is especially true for IoT networks that extend across vast (often continental or global) distances.
To keep communications secure, traditional networks make use of a complex setup of dedicated endpoint clients needed to establish a VPN connection or use SSL/TLS encryption between the various IoT endpoints and the application that processes their data.
Unfortunately, this topography is no longer up to the task of securing communications due to the exploding number of new devices being added to the IoT, enabled by new connectivity models such as Wi-Fi and Zigbee, and the overall miniaturization and low cost of these devices.
Manufacturers will need to deploy their connected devices over a cellular network wherever Wi-Fi is not a practical solution. This has been further complicated by the emergence of software-as-a-service (SaaS) applications and the need to securely transport large volumes of device traffic into the cloud. Cellular-enabled IoT applications require a new approach to both network topology and security technology.
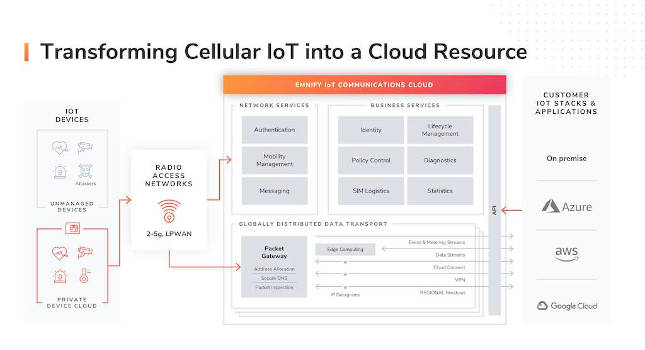
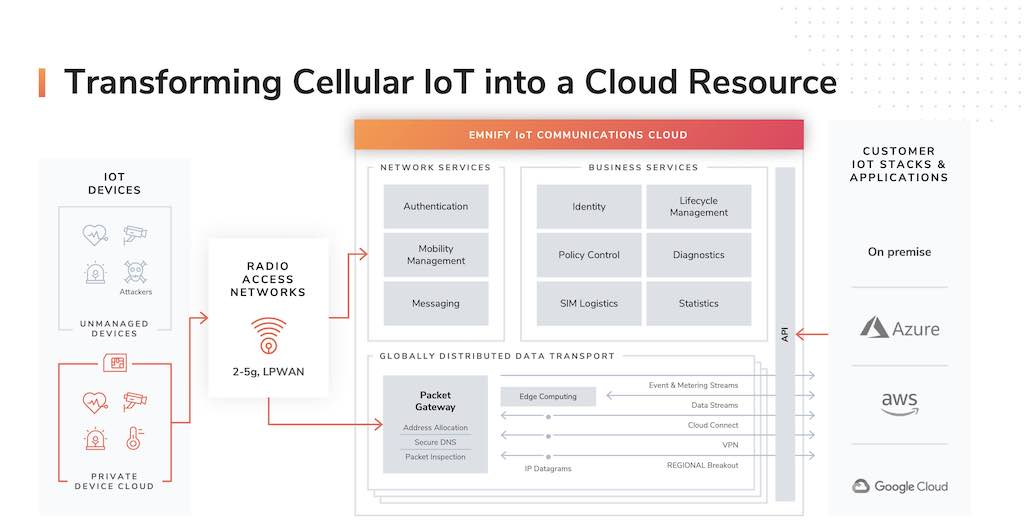
A dedicated IoT cloud emerges
The shortcomings of the prevalent approach have led to the design of a new model: the communications platform as a service (CPaaS). Companies need a dedicated cloud that is optimized for managing and processing thousands of connected IoT devices. CPaaS offers unique advantages. A CPaaS provides companies with application programming interfaces (APIs) so they can integrate communication channels into their applications.
While the model was originally designed for a person-to-person context, CPaaS has evolved to cater to the various technical requirements of IoT applications. With CPaaS providing the stack architecture for IoT applications, it became clear a better security approach was needed.
SASE goes great with CPaaS
The SASE concept is characterized by a global cloud-native architecture, identity-driven services, central policy control, and distributed security enforcement. Using SASE, organizations can integrate their network and security tools into a single management console. This gives them greater visibility of all their traffic and communications.
Originally developed to suit the changing requirements of a remote and globally distributed workforce that required access to enterprise IT infrastructure, SASE came into its own as the best way to manage IoT devices.
Multiple virtualized networking and security applications are converged through SASE into one unified cloud service offering. A centralized policy control system helps to deliver secure access to clients by offering optimized data routing and the protection of communications traffic to the various individual applications. This is independent of where the device, network, and IoT application are located.
SASE is optimized for IIoT applications
The SASE model differs from traditional networking models in several ways. First, it locates security checkpoints closer to the original data source. Next, the various policies (such as access protocols) are administered at distributed points of presence (PoP). These PoPs can be a SASE vendor’s data centers or cloud regions, if located in relative proximity to the device in question. Access is granted upon verification of the identity of the IoT device. A device can be identified based on specific attributes or its location. Furthermore, the policies themselves are programmable and can be tailored to the needs of individual applications.
A SASE combines a cloud-based and centralized system for policy management, as well as local enforcement of identity-driven services, giving users the best of both worlds. Using the cloud clarifies cost and complexity, because all network security services can be consolidated using one vendor, which allows users to have a comprehensive overview of all communications among managed devices.
SASE differs from traditional network security models in other important ways:
Remote access to on-premises resources: Whereas traditional models depend on VPN technology and SSL encryption or make use of a dedicated endpoint client, SASE acts as a VPN replacement. As part of this, IoT devices connect to a SASE to access on-premises or cloud services and the relevant policies are defined and applied through the SASE API.
Access to cloud resources: In a traditional network setting, cellular access of IoT devices to cloud resources are treated like any other online asset, using traditional firewalls, proxies, and normal access to the public internet. A SASE, on the other hand, provides IoT devices with optimized, streamlined, cloud-aware network access.
Networks and internet access: It is complicated to access a cellular network through a traditional software-defined wide area network (SD-WAN) enterprise architecture. A SASE service integrates cellular access and traffic optimization capabilities into a cloud service. This facilitates connectivity between devices.
Backend application security: In the traditional model, firewalls, or web application firewalls (WAF), and backend services are often separate and distinct applications or platforms, which makes integration cumbersome. A SASE provides policing and identity-based access control from a central location, giving users a comprehensive view of network topology and activity.
Network access control: Standalone IoT devices rely on local configuration settings and software components to control network activity. Instead, SASE services aggregate several network security and access control—including firewalls as a service—into one unified fabric.
A modern SASE architecture can deliver a whole gamut of different network and security features. However, these may vary across different vendors’ offerings. The following considerations may be relevant for some manufacturers:
Dynamic data routing with SD-WAN: Using SASE, network access and traffic optimization are integrated in an infrastructure setup distributed across the globe and makes use of multi-regional PoPs. Having access control and security policy enforcement as a cloud-based service, eliminates the need for users to divert communications traffic through a vendor’s own network. Routing data instead to a SASE PoP located in proximity to the device reduces the latency of the IoT application in question.
Firewall as a service (FaaS): Using a cloud-based FaaS is an effective solution to filtering out unwanted and potentially malicious internet traffic and thereby protecting services delivered on the edge.
Cloud access security broker (CASB): A CASB secures transmissions into multiple cloud environments against eavesdropping, traffic sniffing and data theft by encrypting them.
DNS security: By enabling users to configure trusted DNS services, a SASE solution helps them to protect the integrity and availability of their DNS.
Threat detection: SASE services also provide users with a complete visibility of the network and drilled-down event metrics to help them do a root cause analysis on any anomalies that may have arisen in their IoT solution.
Getting started with CPaaS and SASE
Companies should start with an audit of their connected devices and ask questions such as:
- What network topography do you use?
- Do you already make use of cellular connectivity for your IoT devices?
- Which devices are at greatest risk and how serious is it?
Companies also should perform a gap analysis to see how the current infrastructure compares with a CPaaS and SASE environment.
If a company’s findings show a CPaaS and SASE environment is superior to your current model, they should consider upgrading. Using the CPaaS deployment model and the SASE security architecture is an effective way to guard against the threats against IoT devices. A SASE enables users to control all IoT data connections to the public internet, an intranet, a SaaS cloud, and to a distributed workforce.
The looming threat of security breaches and the increasing prevalence of actual intrusions into company networks make it imperative for any manufacturer that depends on IIoT devices to harden their defenses. A successful security breach can have devastating consequences for any company. The selection of state-of-the-art security technologies such as CPaaS and SASE can give manufacturers—and their supply chain partners—assurance they are better protected.
Martin Giess is CTO and co-founder of EMnify. Edited by Chris Vavra, web content manager, Control Engineering, CFE Media and Technology, [email protected].
Keywords: communications platform as a service (CPaaS), secure access service edge (SASE)
CONSIDER THIS
What immediate benefits could you get from CPaaS and SASE?
ONLINE extra
Connect with Martin Giess on LinkedIn.