How overlooking industrial assets creates security risks and what organizations can do to protect their operations.
IIOT and OT cybersecurity insights
- While organizations commonly secure traditional IoT devices, they frequently neglect vital operational technology (OT) assets like PLCs, HMIs, AGVs, and control systems.
- Many companies deploy advanced intrusion detection tools, but OT teams often struggle to effectively use them due to a lack of cross-functional understanding.
- Organizations must go beyond traditional cyber tools and treat industrial cybersecurity like preventive maintenance — proactively monitoring for operational anomalies.
While many organizations invest heavily in protecting traditional IoT devices, they often overlook crucial industrial assets that could pose significant risks to their operations.
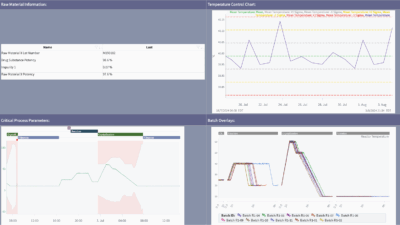
The widespread adoption of OT intrusion detection systems in manufacturing facilities has enabled organizations to build asset inventories and identify potential vulnerabilities through machine learning and AI. However, a concerning gap remains in how these technologies are being implemented. The gap typically evolves who is the actual owner and is responsible for OT devices. OT devices are almost never under IT’s direct control and responsibility.
Finding IIoT and OT cybersecurity gaps
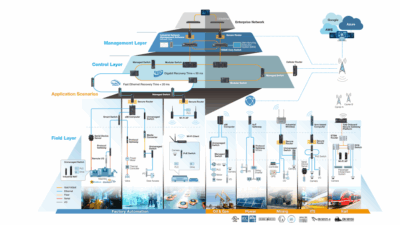
Most organizations focus their security efforts on common network-connected devices like cameras, thermostats, and printers, while overlooking critical industrial equipment. The monitoring of PLC’s, HMI, Engineering programming workstations, the control network, drives, motor control centers, automated guided vehicles (AGVs), robots, and pumps often falls by the wayside, creating significant blind spots in industrial security.
A dangerous misconception persists that industrial control systems are isolated from external threats. As industrial cybersecurity expert Dino Busalachi points out, even standalone machine centers maintain various forms of connectivity, whether through remote access systems or on-site technician interventions. This reality creates vulnerabilities that many organizations are ill-equipped to monitor or address.
The implications of these security gaps extend far beyond traditional cybersecurity concerns. Ignoring industrial IoT assets isn’t just a blind spot – it’s a potential catastrophe waiting to happen, with risks ranging from millions in downtime costs to potential physical harm to individuals.
Security in industrial environments requires a broader perspective that encompasses both cybersecurity, process integrity and safety. While traditional security tools focus on detecting malware signatures and cyber threats, they also play a crucial role in developing asset listing associated risk (vulnerabilities), inventory, monitoring and maintaining operational efficiency.
The parallel between digital security monitoring and preventive maintenance is obvious – just as organizations use sensors to detect thermal, harmonic, or vibration anomalies, they need similar systems to identify disruptive digital behaviors and activities that could impact their assets.
One of the primary challenges in implementing comprehensive industrial security lies in the disconnect between IT and OT teams. Many organizations have invested in sophisticated OT cybersecurity intrusion detection tools and solutions, but their operational technology teams often struggle with to derive value from these investments. This gap stems from a lack of understanding plant operations & processes to determine the platform capabilities and their potential impact on daily operations.
The path to better industrial security requires organizations to find the right partners – experts who understand both the network infrastructure and the automation environment, while maintaining proficiency in the latest security tools and technologies. This expertise becomes particularly crucial as manufacturing environments grow increasingly connected and complex.
Looking ahead, organizations have two main paths to strengthen their industrial security posture. IT departments can proactively build relationships with equipment suppliers, plant builders, and control system designers to better understand the operational environment. Alternatively, OT teams can take the lead in developing security expertise and implementing appropriate tools and processes.
Success in industrial cybersecurity ultimately requires a balanced approach that combines comprehensive security tools with deep operational expertise. As manufacturing environments continue to evolve, bridging the gap between IT and OT becomes not just beneficial but essential for maintaining both security and operational integrity. Organizations must recognize that protecting industrial assets is just as crucial as securing traditional IT infrastructure and take appropriate steps to address both aspects of their security strategy.
5 steps to streNgthen OT security
To help organizations better secure their industrial environments, here are five essential steps to strengthen IIoT and OT security:
1. Conduct a Comprehensive Asset Inventory
Begin by documenting all connected devices, not just traditional IT assets. This inventory should include industrial equipment like drives, motor control centers, AGVs, robots, and PLCs. Pay special attention to identifying equipment that may have remote access capabilities or require vendor support. These present additional security considerations.
2. Bridge the IT/OT Knowledge Gap
Create cross-functional teams that include both IT security experts and OT specialists. Regular collaboration sessions can help both teams understand each other’s priorities and challenges. Consider implementing training programs that help IT teams understand industrial processes and OT teams grasp cybersecurity principles. Bring in a seasoned expert or partner to assist with facilitation of these discussions. The client’s OT Ecosystem of suppliers need to be included in the strategy of OT Cybersecurity
3. Implement Proactive Monitoring Systems
Deploy monitoring solutions that can detect both cybersecurity threats and operational anomalies. These systems should track not only traditional security metrics but also process integrity indicators. Just as organizations monitor equipment for mechanical issues, they should implement similar vigilance for digital behaviors and network activities.
4. Establish Vendor Management Protocols
Develop strict protocols for vendor access and remote support. This includes documenting all third-party connections, implementing secure remote access solutions, and maintaining an audit trail of all external interactions with industrial systems. Regular reviews of vendor access rights and security practices should be conducted.
5. Build Security into New Projects
For new facilities or equipment installations, incorporate cybersecurity requirements into the initial design phase. Work with system integrators and equipment suppliers who understand both operational requirements and security best practices. Ensure that security considerations are part of the architectural engineering and construction process from the beginning.
Success in industrial cybersecurity ultimately requires a balanced approach that combines comprehensive security tools with deep operational expertise. As manufacturing environments continue to evolve, bridging the gap between IT and OT becomes not just beneficial but essential for maintaining both security and operational integrity.
Organizations must recognize that protecting industrial assets is just as crucial as securing traditional IT infrastructure and take appropriate steps to address both aspects of their security strategy.