How endpoint OT security asset management improves a CISO's ability to deliver measurable and rapid improvements to OT cybersecurity.

In information technology (IT), organizations have options to choose from to discover and aggregate asset information. In operation technology (OT), security asset management – discovery, inventory, risk evaluation, etc. – is more difficult given the distributed and sensitive nature of the devices and physical processes controlled by these assets as well as the fact that most run embedded operating systems rather than traditional IT operation systems (OS). The primary reason for the CISO’s frustration is the continued reliance only on network traffic data and protections in OT. Due to fear and uncertainty of operators (in part encouraged by the OEMs that supply the industrial controls hardware), security teams are managing OT security with one arm behind their backs.
The purpose of this blog is to focus on the benefits of an endpoint-focused approach to OT security asset management – one that mirrors the efforts in IT, but done safely and effectively within OT environments.
Challenges of current approaches to OT security asset management
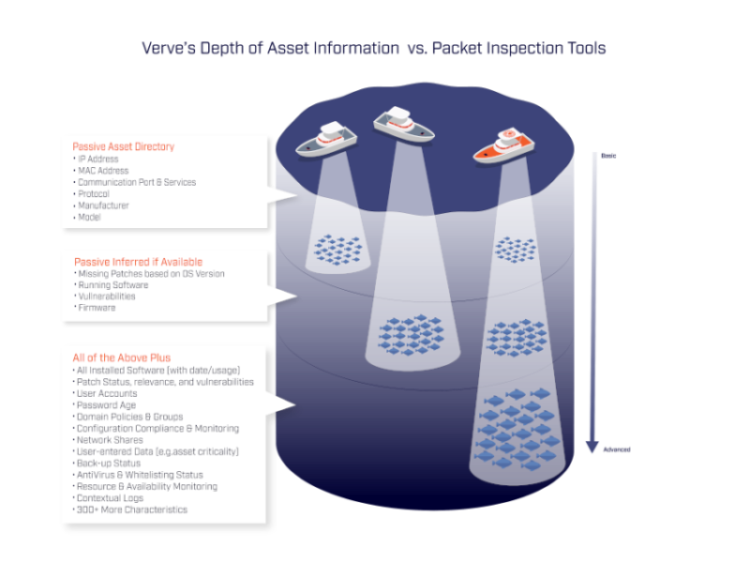
Security asset management is an emerging practice. The primary focus is consolidating the security of a company’s assets into a single database. This includes aggregation in two dimensions: all assets and all security elements of those assets. So OT security asset management would include a comprehensive view of ALL assets within the OT environment, from Microsoft Windows servers and human-machine interfaces (HMIs) to programmable logic controllers (PLCs) and protective relays, variable frequency drives, firewalls and switches, etc.
The second dimension is a comprehensive view of ALL security controls, from patch and vulnerability status to user and account risks, anti-virus and whitelisting status, backup recency, configuration status, etc.
The two traditional approaches to OT asset inventory or visibility have significant drawbacks. The first option is to gather information manually at a site-by-site level. Operations personnel maintain an Excel or similar database of asset information. On a “regular” basis, those resources update the database with new assets that connect. And on a “regular” basis, this list may be audited to ensure accuracy. In some cases, this list is consolidated by centralized resources into a common list. The drawbacks of this approach are obvious. In short, the list is almost always incomplete and out-of-date. And in most cases, this limited and inaccurate information is stuck in a spreadsheet at the plant level.
The second option was to use network-based discovery tools to try to get a picture of the asset information based on analyzing packets that transfer through spans and taps connected to network switches. This option perhaps has less obvious challenges, but challenges remain.
In many cases, the collecting devices do not see assets that do not communicate up to the networking devices where collectors or spans exist. In many cases, seeing all the traffic requires significant investments in collectors, cabling, taps, etc. which may not be sustainable. Further, even if traffic does get picked up, that traffic will not include the most critical security aspects of the device such as firmware or patch status.
Finally, even if it does contain that basic information, it will never contain other critical security information needed for robust security asset management such as all the users and accounts, all installed application software, anti-virus or backup status, etc.
Endpoint-focused OT security asset management
The alternative approach is what we call “endpoint-focused” OT security asset management. The endpoint approach uses OT-specific endpoint visibility and inventory techniques to gather asset information directly from the endpoints themselves and integrates with other security components to complete the security picture.
The endpoint approach to asset management uses OT-specific agent technology tuned to operate safely across all OEM vendor systems combined with an agentless device interface to gather information directly from embedded OT assets. Instead of relying on traffic to expose information about the asset or relying on irregular and inaccurate manual approaches, the endpoint solution gathers the information needed directly from the asset itself.
The OT agent passively collects hundreds of pieces of information about OS-based devices. This includes everything from relevant missing patches, vulnerabilities, 100% of installed application software, all users and accounts even those that are dormant, full configuration settings, current backup status, antivirus, whitelisting status, etc.
Some have expressed concern about an “agent” in an OT environment. In this case, the agent is specifically designed and tested for operational reliability on all OT OEM systems. It has been in use for 15 years on this range of systems with no negative operational impact. The reason is that it is tuned specifically for safety in OT, squeezed down to absolute minimum resource requirements, no inbound ports required, etc.
The agentless device interface delivers accessibility to the range of embedded devices in an OT environment. These devices communicate via hundreds of different OEM protocols and run proprietary OS’s with limited memory. Therefore, agents are impractical, and the agentless interface needs to communicate from a single platform in these different protocols.
The interface communicates with each asset individually in its own protocol, so it can retrieve the critical security information required, without relying on that information is visible in the packets and without the need for an operator to connect to that device through its HMI to stimulate the communication. The agentless interface gathers dozens of different asset information – from mac/arp/cam tables from switches, make, model and firmware versions, as well as full running configurations on networking and many OT devices.
Together, these two elements provide a very deep set of information on ALL assets that is consistently and accurately updated essentially on a real-time basis.
Four benefits of endpoint-focused OT security asset management
CISOs are pressed to increase the security maturity of their OT environments and provide a comprehensive picture of the risks, not to mention compliance against critical standards such as the new TSA requirements for pipelines, rail, marine, etc. OT requires a distinct approach to applying security remediation, however. Endpoint-focused security asset management is a key enabler of achieving these goals for several reasons.
1. Accurate security and compliance data
The TSA OT cybersecurity regulations are only one example of new OT regulations emerging around the world. The increasing threat landscape has driven governments to respond with more prescriptive regulatory requirements.
Compliance requires certain and timely data. Compliance also requires efficiency in gathering and managing the reporting of that data. Even for organizations that have no compliance requirements, boards, C-suites and insurers require accurate and up-to-date OT security asset management information.
To accomplish this, the endpoint approach does not rely on the vagaries of network traffic or manual collection to capture asset information. The data is automatically updated on a timely basis. The system goes directly to the endpoint itself and gathers the data, so there is no need to rely on the uncertainty of whether the data for an asset is picked up in the packet.
2. Lower cost
Second, the endpoint approach enables efficiency in both the collection and reporting of this information. No expensive and hard-to-manage collectors and spans/taps are required. Nor is any manual labor necessary. But perhaps most importantly, ALL of the security information necessary is contained in a single enterprise database.
There is no need to chase down anti-virus information from one (or multiple in the case of a multi-OEM environment) tool, then gather configuration information from another, backup information, log data, etc. each from its own database. The endpoint approach brings all of this centrally into one database for enterprise visibility across global sites and assets driving an over 70% increase in efficiency.
3. 360-degree risk management
OT security requires a comprehensive view of asset risks – perhaps even more that IT where traditional remediation is more straightforward. In many cases, patches cannot be applied on a regular basis because those patches may cause operational disruption on older systems, or they may require reboots which are not possible on devices running 24/7. Similarly, organizations may not be able to update AV signatures as rapidly as in OT and they may require multiple AV tools depending on each OEMs testing and approval.
These unique factors require what we call a 360-degree approach to security management. If you cannot apply a patch, then you need visibility into the rest of the mitigating controls on that asset to ensure you have a way to mitigate that threat. Similarly, if the asset security is dependent on network protection, you need to know that that network device is configured as designed to ensure the protection is in place.
The endpoint approach gathers all of the required asset information to conduct this complete 360-degree analysis – and provides a comprehensive risk score for each asset.
4. OT-safe remediation actions
Proper security asset management requires that an organization actually take remediating actions. But in OT, those remediation’s need to follow proper industrial controls engineering processes. We’ve leveraged our 30 years of controls expertise to build a platform that enables the organization to “Think Global, but Act Local.”
For proper risk analysis and prioritization of remediation or mitigating measures, the platform must enable global analysis as well as “automation” of response actions. However, those actions should go through “local” engineers that know the specifics of the process before the automated action is initiated. The “Act Local” adaptation of remediation accelerates response but includes critical OT safeguards.
– This originally appeared on Verve Industrial’s website. Verve Industrial is a CFE Media and Technology content partner.


