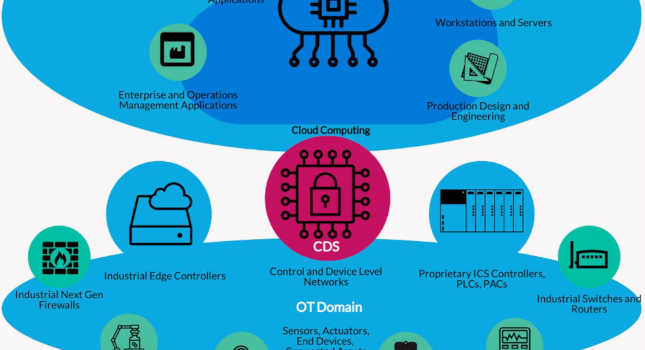
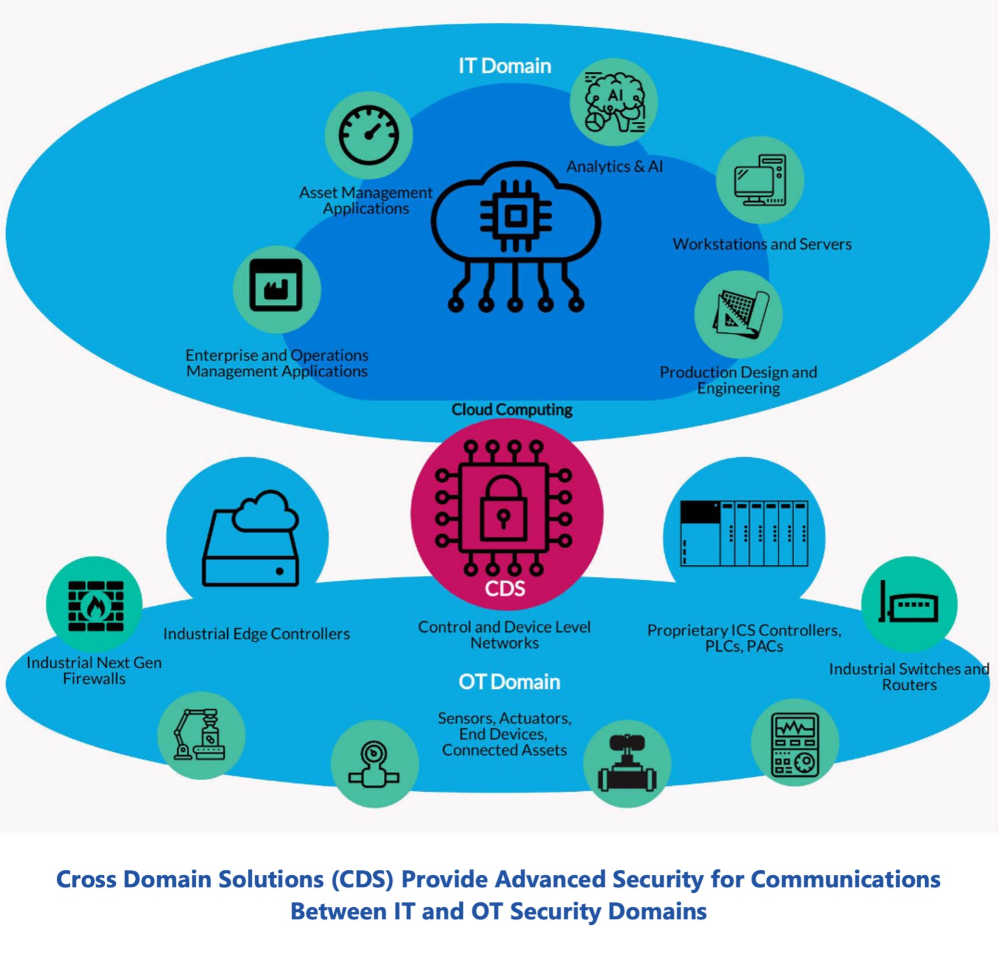
Cross-domain solutions (CDS) can help secure communications between information technology (IT) and operational technology (OT) domains.
Learning Objectives
- Unplanned downtime is a major problem for manufacturers and critical infrastructure, and cybersecurity lapses are a growing cause.
- A cross-domain solution (CDS) manages secure communications between IT and OT domains.
- A common use case for a CDS is replicating process historian data to the enterprise, either on the business network or to the cloud.
Cybersecurity Insights
- Cross-domain solutions (CDS) can help manage secure communications between information technology (IT) and operational technology (OT) domains and keep both sides secure from a cybersecurity attack.
- As attacks against OT increase, they are becoming a major source of unplanned downtime and depending on the industry and the type of attack, the reverberations can go well beyond the source and extend to everyday life, as attacks on Oldsmar and Colonial Pipeline showed.
Cyberattacks and incidents are becoming a major source of unplanned downtime for industrial and critical infrastructure applications. IT-level cyberattacks on business networks can have negative consequences for operations. As was shown with the Colonial Pipeline incident, loss of visibility into the supply chain resulted in an operational shutdown that cost the company millions. Proper isolation of IT and OT domains reduces the chances of an IT level attack impacting OT level operations.
The world of OT and industrial control systems (ICS) is becoming even more integrated with business and enterprise level applications through digitalization and new Industrial Internet of Things (IIoT) technologies, such as cloud and edge computing, IoT protocols like message queuing telemetry transport (MQTT), analytics and machine learning (ML). This expands the threat surface of OT forcing end users to ensure the OT domain is isolated from the world of IT and enterprise systems.
What’s required today is “isolation with communication.” The OT domain must remain secure and isolated from the IT domain to ensure worker health and safety and mitigate unplanned downtime, which costs the industrial and critical infrastructure segment over a trillion dollars a year in lost production. However, segmentation cannot eliminate communication; communication between the IT and OT domain is necessary to realize IIoT benefits.

Cross-domain solutions (CDS) are an excellent way to manage secure communications between IT and OT domains. ARC analysts recently discussed CDS offerings for the industrial and critical infrastructure space with Owl Cyber Defense. Key takeaways include:
- Cyberattacks are now a major source of unplanned downtime.
- Much of the OT level downtime experienced in recent cyberattacks stems from OT level impact resulting from IT level attacks.
- Industry and critical infrastructure need to secure the OT domain and shield it from the negative impact of IT level attacks.
- CDS, long used in the government and defense sectors, are now being applied by industry and critical infrastructure to provide isolation and secure communication between IT and OT domains while preserving the ability to communicate bidirectionally.
Cyberattacks are a major source of unplanned downtime
Unplanned downtime is a major problem for manufacturers and critical infrastructure. ARC estimates unplanned downtime represents more than a trillion dollars in lost revenue worldwide for the industrial and critical infrastructure sectors. In a refinery, an unplanned shutdown can wipe out annual profit. An unplanned power outage can present extreme risks like loss of life and interruption of essential services. In the past, most unplanned downtime could be attributed to operator error or some unexpected or abnormal situation in the process being controlled.
The impact of recent cyberattacks on operations shows cyberattacks and incidents are now a major source of unplanned downtime, one that also presents a risk to human lives, safety, and the environment. According to the US government, the losses suffered in the NotPetya ransomware attack were more than $10 billion.
IT-level attacks have OT-level consequences
Many of the losses suffered during NotPetya were from industrial, manufacturing and critical infrastructure companies that had to shut down operations because of being attacked at the IT and enterprise level. Companies such as Honda, Maersk, Merck and Mondelez International all suffered OT-related losses and significant unplanned downtime. Maersk suffered between $200 and $300 million in losses because it had to shut down shipping operations. Merck is reported to have suffered $135 million in lost revenue and spent over $800 million remediating the effects of NotPetya and upgrading its cybersecurity.
Operations must be secure from IT and enterprise
Most of the technological advancements in OT level systems over the past decade have focused on seamless integration between OT and IT or business/enterprise level functions. The flow of data from the OT world to the IT world has expanded exponentially over the past decade with the influx of IoT. Cybersecurity protection, however, has not kept pace. Despite large-scale deployment of a myriad of cybersecurity products and solutions, IT level cyberattacks still have OT-level consequences.
Cross-domain cybersecurity solutions benefits for OT
Defense and high sensitivity government applications have long used CDS, where absolute security is necessary. CDSs ensure secure communications between trusted and untrusted domains.
A CDS is an integrated information assurance system that can consist of both hardware and software. CDSs provide a controlled interface to manually or automatically enable or restrict the access or transfer of information between two or more security domains based on predetermined security policies. CDSs enforce domain separation and often include some form of content filtering, which is used to designate information unauthorized for transfer between security domains or levels of classification.
Originally, CDSs were deployed in the military, intelligence and critical infrastructure sectors where a breach cannot be tolerated and can cost lives. CDSs also have typically passed a rigorous testing process administered by the National Cross Domain Strategy Management Office (NCDSMO), a unit of the National Security Agency (NSA).
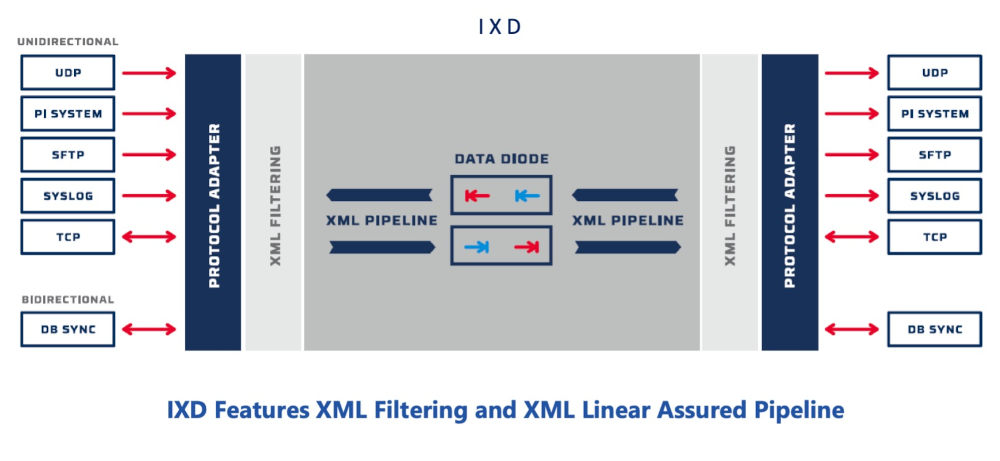
CDS cybersecurity components
CDS cybersecurity solutions consist of a combination of hardware and software using a hardened operating system and specialized tools like Security-Enhanced Linux. CDSs provide multiple layers of filtering and content inspection and provide a “protocol break” (in the form of a data diode), to enable secure connections between trusted and untrusted network domains.
Cybersecurity: Choosing between a CDS or firewall
Industrial firewalls are ubiquitous in the world of industrial control systems. Most industrial facilities use firewalls to protect perimeters and provide zone segregation. However, firewalls have numerous vulnerabilities and require ongoing configuration and maintenance efforts. Firewalls are a great way to provide network security and should not be confused with a CDS. It is because of the vulnerabilities inherent in firewalls and other security offerings that CDSs were developed.
Another key difference between CDS and firewalls is long-term operational and maintenance costs. Firewalls require ongoing maintenance. Firewall rulesets must be periodically reviewed, regular firewall security audits should be done, firewall rulesets must be backed up, and firewall logs must be periodically reviewed.
CDSs have fewer rules to configure and less ongoing maintenance requirements. Where a firewall is more analogous to a deny-list strategy, where certain protocols and ports and services are blocked. A CDS operates more like an allow list where only certain kinds of communications and services are allowed. This is what makes CDSs so useful in supporting things like mandatory access control (MAC) schemes and role-based access control (RBAC).

CDSs are adopted by many industries to help cybersecurity
CDSs are moving beyond the world of defense and government applications and are being used across many industries. The hydrocarbons sector is the largest adopter today, from oil and gas exploration and production to pipelines and liquefied natural gas (LNG) applications. The downstream sector, including refining and petrochemicals, also are adopting the technology. CDSs also are being used in the chemicals, automotive and power generation industries.
End users are deploying CDSs to achieve the highest level of security in communication between OT and IT domains. The amount of OT data being consumed at the IT and enterprise level continues to expand exponentially. Firewalls by themselves are not enough to provide the proper level of isolation between OT and IT domains.
Another common use cases for CDSs in industrial and infrastructure applications is replication of process historian data to the enterprise, either on the business network or to the cloud.
Cybersecurity benefits of a CDS
As the demand for more secure communications mounts between the world of OT and IT, end users should consider CDS to provide better isolation and security of communications between these two domains. The lower operational and maintenance costs and requirements of CDSs combined with the level of security provided can make a cost-effective strategy for avoiding unplanned downtime at the OT level if an attack happens at the IT level. CDSs also can prevent against attacks launched at the OT level pivoting to the IT network or cloud.
Larry O’Brien is vice president at ARC Advisory Group, a CFE Media and Technology content partner. Edited by Chris Vavra, web content manager, Control Engineering, CFE Media and Technology, [email protected].
MORE ANSWERS
Keywords: cross-domain solutions, IT/OT convergence
ONLINE
https://www.industrialcybersecuritypulse.com/
See additional IIoT and Industry 4.0 stories at https://www.controleng.com/iiot-industrie-4-0/
CONSIDER THIS
How can a CDS help improve OT security at your facility?


