Cybersecurity maturity and optimization are crucial as attacks against operational technology (OT) continue increasing.
The closing months of 2020 saw a 45% increase in cyber-attacks targeted towards healthcare organizations. Healthcare providers of all types and sizes have been breached. A report by Black Book Market Research predicts that data breaches in the healthcare industry are likely to triple in volume in 2021. In fact, the recent SolarWinds breach and its ripple effect has left many organizations concerned.
So, how does an organization prepare itself to securely operate in today’s dynamic environment? A simple answer would recommend an organization to increase its focus on cybersecurity “management” and make it a strategic priority. One cannot underestimate the importance of good management, especially knowing that more than 85% of cyber-incidents involve human-factors and 65% of incidents originate by internal actors or partners. There are three key elements to good cybersecurity management – strategy, operational excellence, and organizational engagement. The recent amendment (signed into a law on Jan 5, 2021) to HITECH further reinforces this opportunity.
The HITECH amendment enables the secretary of HHS to potentially reduce penalties and the length as well as extent of audits for those breached entities that had a cybersecurity program with a recognized standard (i.e., NIST, HHS Guidelines, etc.) in place for at least 12 months. Penalties and investigations cost about 33% of total cost of an incident. Data suggest that an incident can cost up to 54% of annual revenue to a $5 million revenue healthcare provider and 4% of annual revenue to $1.5+ billion revenue entity.
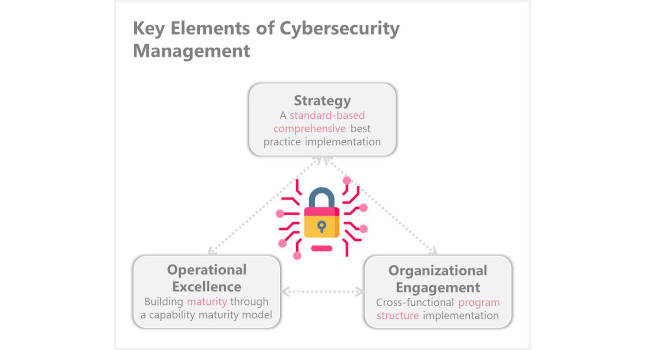
Three key elements of cybersecurity management
1. Cybersecurity strategy. Cybersecurity efforts have predominantly followed individual use cases enabled by specific technical tools. This approach has led to inefficient capital deployment and mixed overall protection for many organizations. Furthermore, many organizations typically delegate cybersecurity efforts only to their internal IT/IS teams or external IT partners. When a large portion of incidents involve human-factors and partners/internal actors are the largest contributors, not involving all employees, functions and partners in the cybersecurity efforts leave many risks unaddressed. A risk-based approach using a standard-driven (e.g., NIST, HHS guidelines, etc.) best practices ensures the required comprehensiveness and good ROI. It also makes it easier to communicate and operationalize the strategy in an organization – “we must adhere to XYZ standard.” The HHS guidelines recommend up to ninety controls for organizations to implement. The guidelines were developed by engaging 100+ industry practitioners that included some off the health system Chief Information Security Officers.
2. Operational excellence. Someone once said, “we are what we repeatedly do. Excellence, then, is not an act, but a habit.” To achieve excellence, an organization has to mature its cybersecurity related practices. Cybersecurity maturity is critical considering organizations nowadays operate in a dynamic environment where M&A, employee turnover, and new technology introductions have become the norm. CMMI framework offers good a way for an organization to measure, manage and mature capabilities. In fact, the US HHS advocated adopting a maturity model in its HC3 Intelligence Briefing on August of 2020. Progressive organizations use Key Performance Indicators (KPI) effectively to institutionalize and mature processes.
3. Organizational engagement. Organizations often operate in functional silos. At the same time, many of the cybersecurity controls span across multiple functions requiring cross-functional engagement. Cybersecurity related technology jargons, however, can be intimidating for many who are not in IT or IS functions. Hence, it is essential for employees to know how their respective roles impact the cybersecurity posture of an organization. By building a cross-functional program structure and institutionalizing an operating rhythm to review progress, leaders can effectively engage other functional participants, help them appreciate their contributions to cybersecurity, mature processes, and build a culture of security.
Overall, a systems engineering approach and good management can make cybersecurity simple, cost effective and a part of the organizational DNA.
– This article originally appeared on Meditechsafe’s website. Meditechsafe is a CFE Media content partner.

