Why manufacturers must embed cybersecurity into system design to ensure smart operations are resilient, reliable and ready for tomorrow's threats.
Cybersecure by design insights
- Cybersecurity must be built into OT systems from the start — not added after deployment — using a proactive, cybersecure-by-design approach grounded in cyber-informed engineering (CIE).
- The ISA/IEC 62443 Automation Solution Security Lifecycle offers a practical framework for applying CIE principles throughout the system lifecycle, ensuring security is integrated at every phase.
- Designing for cybersecurity from Day One improves resilience, minimizes downtime, protects sensitive assets and supports faster innovation and deployment in smart manufacturing.
As manufacturers integrate new technologies across the plant floor, cyber threats are escalating just as fast. Too often, cybersecurity for operational technology (OT) assets is addressed after deployment, or worse, after a breach. But in today’s highly connected plant floor environment, this type of reactive model is no longer sufficient.
Instead, true protection demands a proactive approach where cybersecurity is embedded into system design from Day One. By applying the principles of cyber-informed engineering (CIE), which emphasize the integration of cybersecurity considerations into every phase of system design and operation, manufacturers can ensure their smart systems are resilient from the start.
Why reactive cybersecurity is no longer enough
In Deloitte’s 2025 Smart Manufacturing and Operations Survey, the organization found that 68 percent of respondents had conducted a cybersecurity risk or maturity assessment in the last year, yet 91 percent still experienced a breach. This disconnect seems to highlight a deeper issue — while compliance exercises are broadly accepted, the hard work of actual security implementation is still a challenge.
To prevent these issues from further escalating as new technologies are implemented on the plant floor, manufacturers must make cybersecurity a core component of their system design. But despite this reality, only 26 percent of manufacturers surveyed say they enforce secure-by-design principles when implementing new technologies, and they do it only when it doesn’t delay deployment. In other words, cybersecurity is still being sidelined in favor of speed and productivity, even if the reality is that inadequate cybersecurity can greatly hinder these metrics when a breach occurs.
The case for cyber-informed engineering
To build resilience into modern manufacturing systems, manufacturers must shift from typical reactive cybersecurity practices, where security measures are not implemented until systems are installed, to a proactive CIE approach. This method recognizes cybersecurity as an essential system requirement, just like performance or reliability, that must be integrated into the conception, design, development and operation of any physical system.
More specifically, CIE focuses on shaping system behavior to limit an adversary’s ability to cause harm, even if a breach occurs. Key principles of CIE include:
- Consequence-driven design: Identify what could go wrong if a system is compromised and eliminate or reduce that risk at the design level.
- Secure architectural segmentation: Isolate high-consequence assets in ways that limit cyberattack paths using zones and conduits.
- Fail-safe design: Ensure systems default to safe modes under anomalous or unauthorized activity.
- Cyber-physical awareness: Recognize that actions in the digital world have real-world, physical consequences.
When the principles of CIE are applied to the design of smart manufacturing equipment, the resulting systems are inherently secure — or, in other words, cybersecure by design. In short, this means:
- Cyber risks are identified and addressed early.
- The system architecture supports security objectives.
- Technical and organizational security controls are part of the base design.
- Recovery, monitoring and resilience are designed into the system, not bolted on afterward.
Let’s now dive into how to leverage the framework identified in the ISA/IEC 62443 series of standards to ensure systems are cybersecure by design.
Using ISA/IEC 62443 to build security into the system lifecycle
The Automation Solution Security Lifecycle as defined in ISA/IEC 62443 aligns directly with the principles of CIE and provides a detailed framework for engineering cybersecurity into industrial automation systems. By mapping out the phases and responsibilities for the key stakeholders of an automation solution — this includes asset owners, system integrators, product suppliers and maintenance providers — this standard helps ensure cybersecurity is adequately addressed throughout every phase of the system lifecycle.
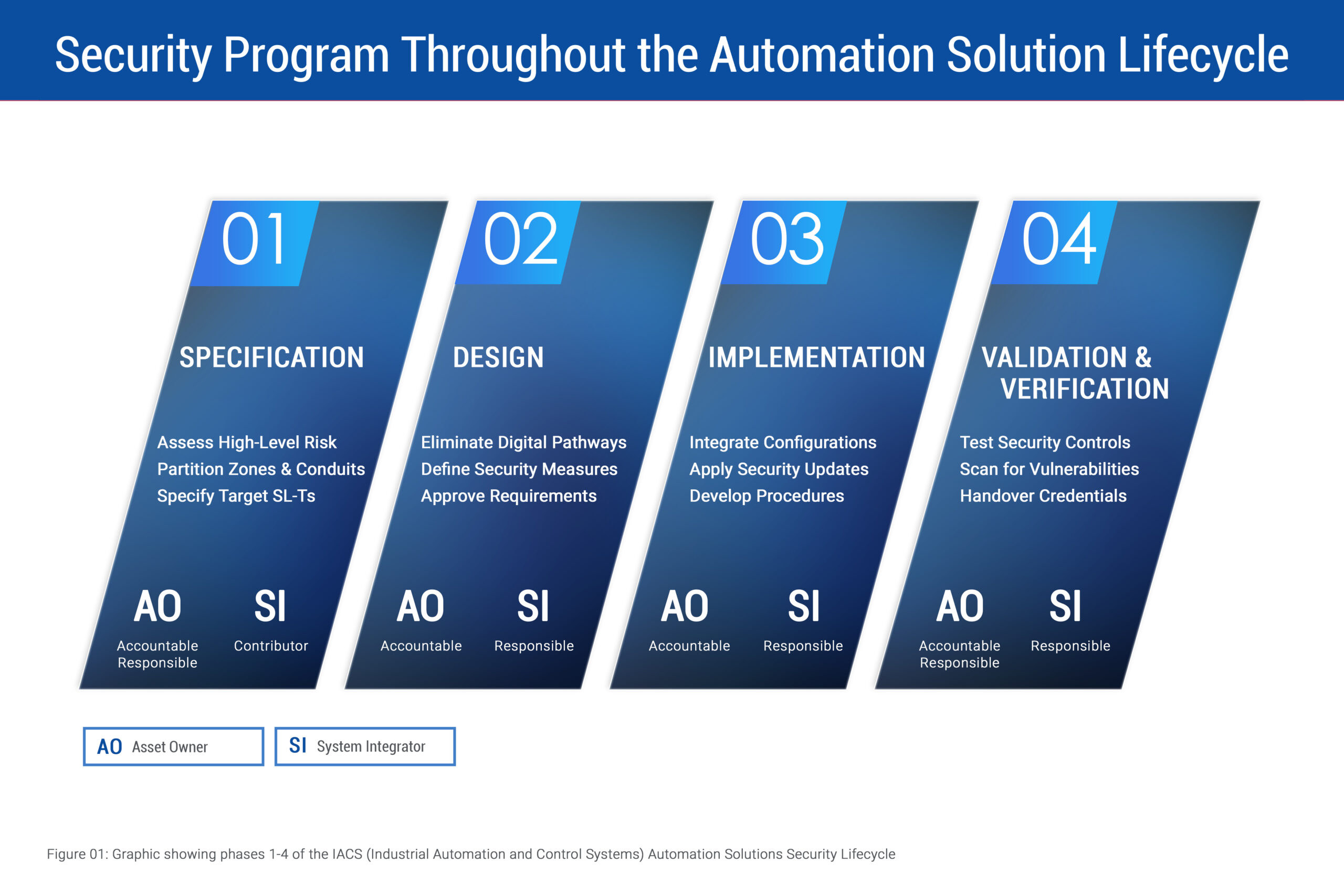
This lifecycle includes seven phases: specification, design, implementation, verification and validation, operation, maintenance and decommissioning. However, for the purposes of this article, we will focus on the first four phases (Figure 01).
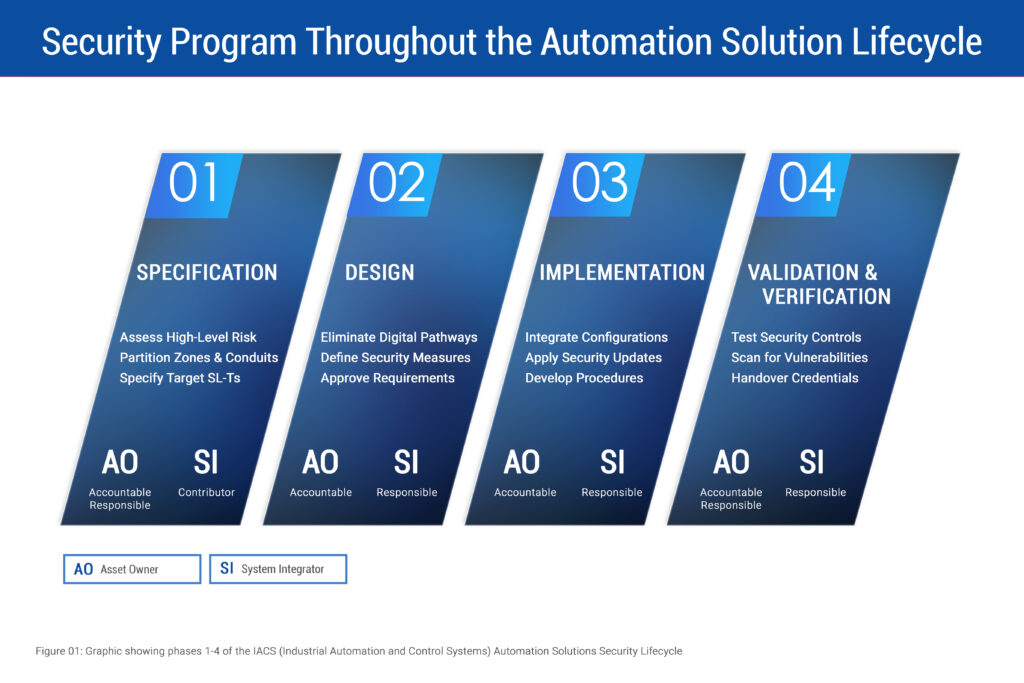
Specification
- Perform an initial, high-level cybersecurity risk assessment of the risks that will exist for the system being designed.
- Partition the system into zones and conduits, which allows security requirements to be tailored and contained and creates baseline security boundaries.
- Specify the target security levels (SL-Ts) for each zone/conduit.
Design
- Conduct detailed risk assessments for each zone and conduit.
- Identify ways to eliminate digital pathways to high-consequence failure modes.
- Define technical security measures that implement protections meeting the SL-Ts.
- Define organizational security measures to address human factors and when technical limitations require compensating controls.
- Document the cybersecurity requirements specification, which must be approved by the asset owner before implementation begins.
Implementation
- Integrate the system components according to the security design.
- Appropriately configure all layers of the defense-in-depth approach, so that a failure of a single layer does not result in failure of the overall protection.
- Apply product security updates during installation.
- Develop supporting organizational procedures for operations and maintenance phases.
Verification and validation
- Conduct tests to ensure all technical security requirements have been met.
- Perform vulnerability assessments and verify access controls.
- Complete formal handover to operations, including credential changes and asset owner validation.
In summary, following the Automation Solution Security Lifecycle as defined in ISA/IEC 62443 can help you design systems using the CIE method since risk assessments are conducted early and revisited regularly, systems are partitioned into zones and conduits to manage and contain cyber threats and security levels are defined, validated and maintained throughout the lifecycle of your system.
The benefits of having cybersecurity as a design requirement
Adopting a cybersecure-by-design mindset is more than checking a box. It’s about making sure the system you’re designing can inherently identify, protect, detect, respond and recover — the core NIST Cybersecurity Framework function — without relying on stopgap controls or manual workarounds.
When done right, cybersecure-by-design systems:
- Sustain uptime by minimizing disruption risk.
- Protect intellectual property and sensitive data.
- Accelerate deployment by reducing the need for retroactive fixes.
- Align with standards like NIST 800-82.
- Support long-term productivity and continuous improvement.
Designing for resilience in the age of smart manufacturing
As manufacturers modernize operations, the digital transformation of the plant floor cannot come at the cost of cyber resilience. With every new sensor, controller or cloud connection, the attack surface grows, and so does the urgency to rethink how cybersecurity is approached.
Embracing the CIE method and the ISA/IEC 62443 Automation Solution Security Lifecycle can provide manufacturers with a practical, standards-based path to shift from reactive defenses to proactive design. When they are applied together, cybersecurity can be approached as an embedded, enabling element of your smart manufacturing efforts.
By engineering systems to be cybersecure by design, manufacturers not only reduce risk, but also gain the confidence to innovate faster, operate more reliably and build a foundation that can withstand both digital and physical threats.
AUTHOR
Timothy Mullen is an OT cybersecurity team lead at Applied Control Engineering, Inc. (ACE), leading projects that identify and remediate cyber vulnerabilities to design new systems that incorporate security as a fundamental principle. His diverse and multidisciplinary background has led to a strong track record bridging the IT/OT gap to achieve security best practices while fulfilling engineered system requirements
Prior to ACE, Mullen worked in commercial nuclear power, performing cybersecurity assessments of plant control system upgrades. His industry experience spans chemical processing, nuclear energy and building automation systems.
Mullen is a licensed professional engineer (PE) in the state of Maryland, a global industrial cyber security professional (GICSP), and holds a B.S. in computer engineering from Johns Hopkins University and an M.S. in computer engineering from Villanova University.
LEARNING OBJECTIVES
- Recognize the role of cyber-informed engineering (CIE) in designing operational technology (OT) systems that are cybersecure by design, not by retrofit.
- Understand how to leverage the ISA/IEC 62443 Automation Solution Security Lifecycle as a framework for embedding cybersecurity into control system engineering practices.
- Identify key design strategies — such as early-stage risk assessment, security zoning and disaster recovery planning — that enhance OT system resilience.
CONSIDER THIS
Is cybersecurity treated as a core design requirement in your organization — or is it still an afterthought that leaves smart manufacturing systems exposed?