A operational technology cybersecurity consultant provides advice in a Pack Expo Las Vegas 2023 session and provides more information about how to improve OT cybersecurity. See video.

Learning Objectives
- Understand the importance of merging operational technology (OT) and information technology (IT) teams together./li>
- Learn how to get everyone on the same page in terms of objectives and priorities and developing a shared plan.
- Watch a short video walking through 5 key pillars of operational cybersecurity.
Operational cybersecurity insights
- Information technology and operational technology personnel can and should collaborate to improve cybersecurity.
- Five key pillars can help improve operational cybersecurity, and it’s important to learn which components are right for an implementation. Are you using at least one from every pillar?
- Do you need cybersecurity consulting help to help avoid or decrease damage from a cybersecurity incident?
Have you done enough to thwart avoid a cybersecurity breach? Do you know what happens when a breach occurs? How long until you’re up and running again, and what will be the likely damages?
Constantine Antoniou, cybersecurity business consultant, Schneider Electric, spoke at Pack Expo Las Vegas 2023 in a presentation called: “Cybersecurity essentials too many CPG firms overlook.” He also talked to Control Engineering and CFE Media and Technology about how greater cooperation between information technology and operational technology experts can lead to greater success when applying five pillars to improve operational cybersecurity. See more information about each below with a video.

Are you getting cybersecurity consulting help?
In Antoniou’s presentation, he discussed how the cybersecurity threat landscape is becoming more sophisticated and can create catastrophic health and safety consequences (photo), operational impacts including loss of control of processes, financial losses related to operational distribution and business disruption, financial loss and reconnaissance or espionage. Worst cases have to deal with injuries, death, damage, property loss and long downtimes. (Photo shows kinds of damage.)
Average downtime is 21 days, average fee for ransom in 2021 was $200,000, with the largest payout at $40 million. Many set ransoms based on insurance document knowledge; of claims filed, an average of 42% covered a fraction of damages. Read the fine print, Antoniou, suggested because in many cybersecurity insurance policies, the big print giveth and the small print taketh away. During COVID-19, there was a 600% growth in malware sent in email. Now ransomware platforms are available on the dark web for hobbyist hackers to use.

IT/OT collaboration improves cybersecurity
While traditional goals of consumer packaged goods (CPG) manufacturers information technology (IT) and operational technology (OT) can differ, it’s imperative these groups collaborate to implement cybersecurity to meet all goals of the organization (IT vs OT photo).
Combined efforts of people, process and technologies are needed to protect operational CPG process and management systems with associated assets from cyber threats to maintain the safety resilience and confidentiality of attached systems and their data.

New government reporting requirements say a report of a cybersecurity breach is required on day two, but most organizations don’t even know details then.
Many organizations have vast amounts of high-value intellectual property (IP) with low tolerance for downtime.
Where is your facility on the cybersecurity map?
Looking at an OT cybersecurity maturity map (photo) may help with understanding who is responsible for what and if there’s the required updated systems and devices inventory of what’s connected. The stages include 1) Awareness 2) Visibility 3) Oh, wow [a cybersecurity event] 4) Firefighting 5) Integration and 6) optimization. Only 10% of organizations are in steps 5 and 6.
Integrating and aligning OT with an IT security operations center (SOC) requires collaboration and can produce better outcomes than when OT and IT are isolated and confrontational.

Looking at security cybersecurity assessment goals can reveal some fairly basic deficiencies, such as firewalls installed but not programmed, providing an organization with visual reassurance, but an easy passthrough for hackers.
Cybersecurity consultants often uses IEC-62443, NIST 800-82 (53 is IT standard) and other standards to help in creating layers of defense appropriate to security risk level goal.
SL3 withstands a sophisticated cybersecurity event. SL4 withstands intentional attacks.

Video: 5 key pillars of operational cybersecurity
A short video with Antoniou goes over five key pillars of operational cybersecurity (photo). Learn which components are right for your implementation: Use at least one from every pillar. At minimum, he advises using one from each.
-
Identify: audits, assessment
-
Permit authentication, authorization accounting, multi-factor identification, segmentation, security remove access, physical security
-
Protect endpoint protection anti-malware, DLP, HIPS, whitelisting, removable media control, patch management
-
Detect security information and event management (SIEM); network performance monitoring, anomaly detection, intrusion detection IPDS
-
Respond: Backup and disaster recover, forensics and incidence response.
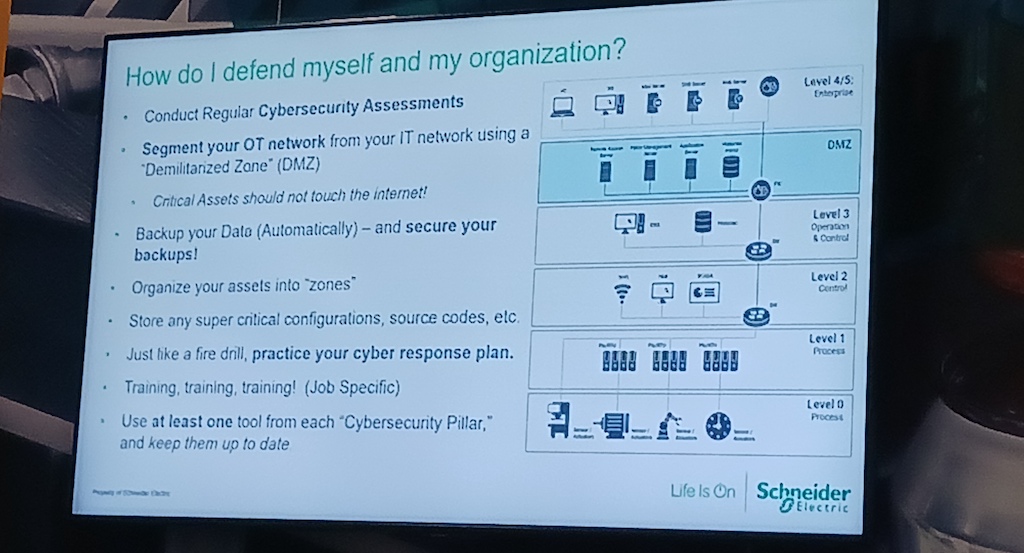
How to lower cybersecurity risk?
Ultimately, an organization has to figure out the best way to defend against cyberattack. One common downfall is storing up-to-date backups in a different, unattainable, secure location. A checklist of final questions (photo) can provide additional perspective about cybersecurity readiness.
Mark T. Hoske is content manager, Control Engineering, CFE Media and Technology, [email protected].
KEYWORDS: Cybersecurity, cybersecurity consulting
CONSIDER THIS
Are your cybersecurity measures enough? How do you know?
ONLINE


