A Dragos report details how Volt Typhoon hackers accessed a Boston-area utility for a year, prompting cybersecurity upgrades.
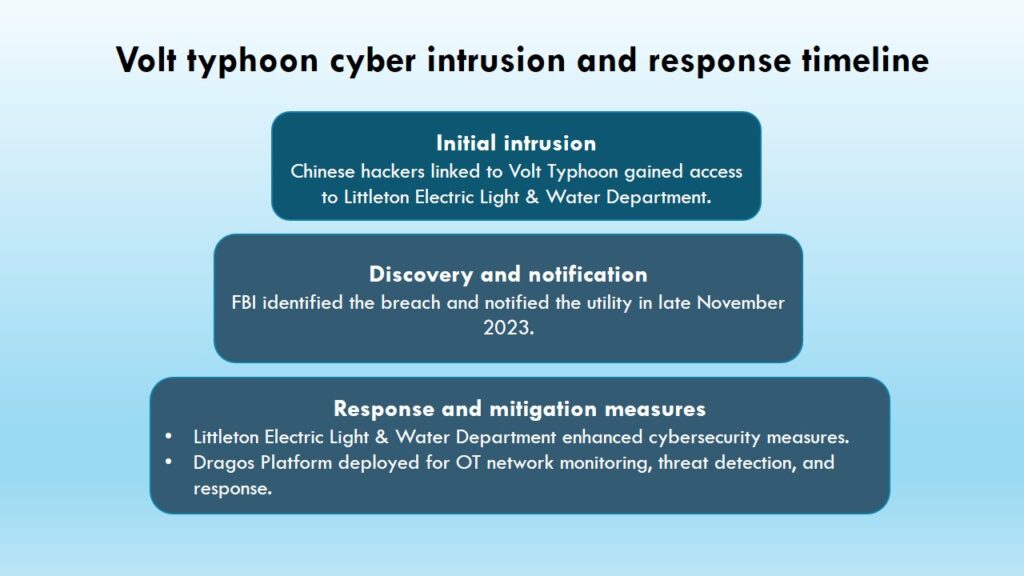
A report published by cybersecurity firm Dragos details how Chinese hackers linked to the Volt Typhoon group maintained access to a major power and water company near Boston, for nearly a year.
The breach at Littleton Electric Light & Water Department occurred between February and late November 2023, when the FBI notified the utility of the intrusion.
The activity was assessed as part of a broader campaign linked to the Chinese government “seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against U.S. critical infrastructure in the event of a major crisis or conflict with the United States,” CISA and the FBI have repeatedly warned.
“The significance of the discovery of this attack is that it highlights that the adversary not only aimed to maintain persistent access to the victim’s environment for a long tenure, but also were aiming to exfiltrate specific data related to OT operating procedures and spatial layout data relating to energy grid operations,” a Dragos expert said.
The incident led to increased cybersecurity measures at Littleton Electric Light & Water Department, resulting in the deployment of the Dragos Platform to improve OT network monitoring, threat detection, and response.
U.S. law enforcement reports that Volt Typhoon has accessed multiple critical infrastructure organizations in the U.S., Guam, and areas near U.S. military bases, potentially to disrupt military operations.
Experts offer perspectives on the matter.
Ted Miracco, CEO, Approov: “Volt Typhoon’s 300-day foothold in the U.S. electric grid was a blueprint for future sabotage. Against nation-state actors this sophisticated, only a Zero Trust, intelligence-driven defense can outmatch their persistence. Assume compromise, segment ruthlessly, and hunt threats before they strike.”
Evan Dornbush, former NSA cybersecurity expert: “Attackers have an unfair and perpetual advantage because they monopolize output from the vulnerability research community. Until defenders can effectively engage the audience that produces the zero day exploits attackers rely on, defenders will always be reacting post-attack rather than taking proactive measures.
“The re-emergence of network threat detection is critical in adversary discovery. While overall I’m an AI skeptic, if there’s one area that continues to show promise, consider investing in AI-based NDR solutions, which Dragos’ marketing team reminds us can be very effective at picking out lateral movement and other abnormal traffic from your network, far more efficiently than log file analysis.”
Dragos focuses on protecting industrial control systems (ICS) and operational technology (OT) from cyber threats and collaborates with government agencies and private sector partners.
Edited by Puja Mitra, WTWH Media, for Control Engineering, from a Dragos news release.