A critical security gap that is widely ignored – the disparity between the attention applied between TCP/IP and serial network devices security.
Cyber attacks on critical infrastructure’s industrial control systems (ICS) are still on the rise due, for the most part, to the increase in cybercrime and geopolitical tensions – tensions that ironically were fueled by a barrage of cyber campaigns focused on compromising essential services over the past decade. Exacerbating the problem is the rate at which the ICS landscape is evolving. Rapid technological advancements such as the Industrial Internet of Things (IIoT) and the strive towards Industry 4.0 mean the attack surface is growing and industries are essentially opening their organizations to increasingly sophisticated threat actors. A report by IBM X-Force Threat Intelligence Index 2020 (reported by securityintelligence.com) found the number of operational technology (OT) attacks increased by over 2,000% since 2018.
Moreover, the significant uptick in attacks is also an alarming indication of the rate at which these threat actors are outpacing our ICS cyber defenses, resources and skills. As security experts focus their attention on nullifying the threats, there still exists a critical security gap that is widely ignored – the disparity between the attention applied between TCP/IP and serial network devices security.
Why ICS have combined TCP/IP with serial networks
From as early as the 1960s, ICS communications were supported by RS-232, RS-485, and RS-422 serial interfaces. Serial protocols such as Modbus, Profibus, DNP3, IEC101, and BACnet MS/TP were developed without security in mind because they were intended to be deployed in highly controlled environments. Plus, OT cyber attacks were not a concern at that time.
The turn of the century however, brought a widespread transformation in OT network architecture, with TCP/IP interfaces becoming increasingly popular – all the while industries were progressively increasing interconnectivity between IT and OT networks.
Nevertheless, despite the large-scale shift in network frameworks, serial-connected devices continued to prevail across ICS environments by primarily occupying ICS’ cyber-physical layer and have consequently become prime targets for motivated threat actors. These legacy devices are not going away and will remain crucial for years to come. This boils down to their long lifespan and how asset owners are averse to the expense and significant downtime associated with replacing them. Likewise, ICS vendors are still choosing to support RS-232, RS-485, and RS-422 serial interfaces because they are reliable, inexpensive and universally supported.
Why serial network security matters
Nowadays, ICS cybersecurity platforms focus on higher-level TCP/IP that control industrial processes, not the actual serial communications between controllers and devices. These are the same devices that control everything from electrical power, pressure valves on natural gas pipelines to chemical regulators used for treating drinking water thus are crucial for safe and reliable essential services.
What security practitioners often ignore is the most significant security challenge lies in these serial-connected field-devices. A majority of serial communications implemented today do not support encryption and authentication of commands and are therefore susceptible to tapping, interception, replay attacks, and unauthenticated command execution. A publication by Idaho National Laboratory entitled Cyber Threat and Vulnerability Analysis of the U.S. Electric Sector (August 2016) cited:
“The communication protocols used throughout ICS networks are of additional concern. Common and long-established ICS protocols such as Modbus and DNP3 used throughout the power system have little or no security measures: lacking authentication capabilities, messages may be intercepted, spoofed, or altered, potentially causing a dangerous event in an operations environment.”
[Robinson, Michael, “The SCADA Threat Landscape,” BCS, September 2013]
Not only are the devices inherently vulnerable to cyberattacks, but their communications data is often missing to higher-level intrusion detection platforms. These security limitations are magnified when the devices are situated at the last line of control; thus, adversaries are now directing their attention towards these harder to access but less secure networks.
Cybersecurity challenges
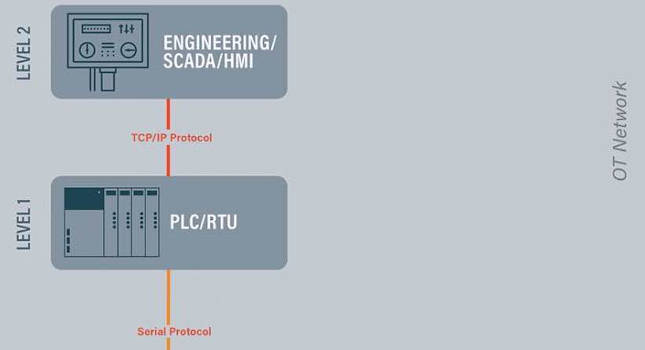
While TCP/IP cybersecurity platforms strengthen OT network defenses, they are not equipped to deal with actual serial-based vulnerabilities. For operations that rely on serial-connected controllers, the platforms only secure network communications down to level 1 (field controllers), and do not monitor or protect communications in the final furlong – which is between the field controllers and field devices (level 1 – level 0).
Additionally, intrusion detection tools monitor data fed from level 1 field-controllers. If adversaries compromise or intercept communications between level 1-0, they could spoof the data to show normal operations while simultaneously exploiting the industrial physical processes i.e. they can spoof clean communication upstream and send malicious communication downstream. This is how Stuxnet successfully exploited uranium enrichment centrifuges in Iran, and the unsuspecting operators only realized something was amiss once the devices were damaged beyond repair.
Courtesy: Cynalytica[/caption]
Closing the cybersecurity, networking gap
The need for reliable ICS monitoring tools has been well documented over the past decade. Publications such as the NIST Situational Awareness for Electric Utilities NIST SP 1800-7 Practice Guide stated:
“To improve overall SA, energy companies need mechanisms to capture, transmit, view, analyze, and store real-time or near-real-time data from ICS”… “The ability to do this will result in earlier detection of cybersecurity incidents and potentially reduce the severity of the impact of these incidents within a utility’s operational infrastructure.”
While there is an array of ICS monitoring tools on the market today, they only provide coverage for TCP/IP networks. In order to get real-time data from serial-connected field devices, operators must capture the data via the serial bus – that is the data being transmitted from the field controller to the field device and vice versa. This will enable them to validate their devices’ behavior and quickly identify anomalous communications.
However, it is important to exercise caution when integrating a monitoring tool to the serial network. Operators must ensure the monitoring device does not interfere with the integrity of the serial line and inadvertently introduce operational risk or latency or create an unnecessary attack vector to the network.
This was originally posted on Cynalytica’s blog. Cynalytica is a CFE Media content partner. Edited by Chris Vavra, web content manager, CFE Media and Technology, [email protected].
Cynalytica, Inc., is a partner member of the Control System Integrators Association (CSIA). For more, visit the company profile on the Industrial Automation Exchange.